Gobysec Goby Versions Save
Attack surface mapping
Beta2.2.0
1 year agoIn this update
Community version update:
- New memory shell plugin
- ShellHub plugin update
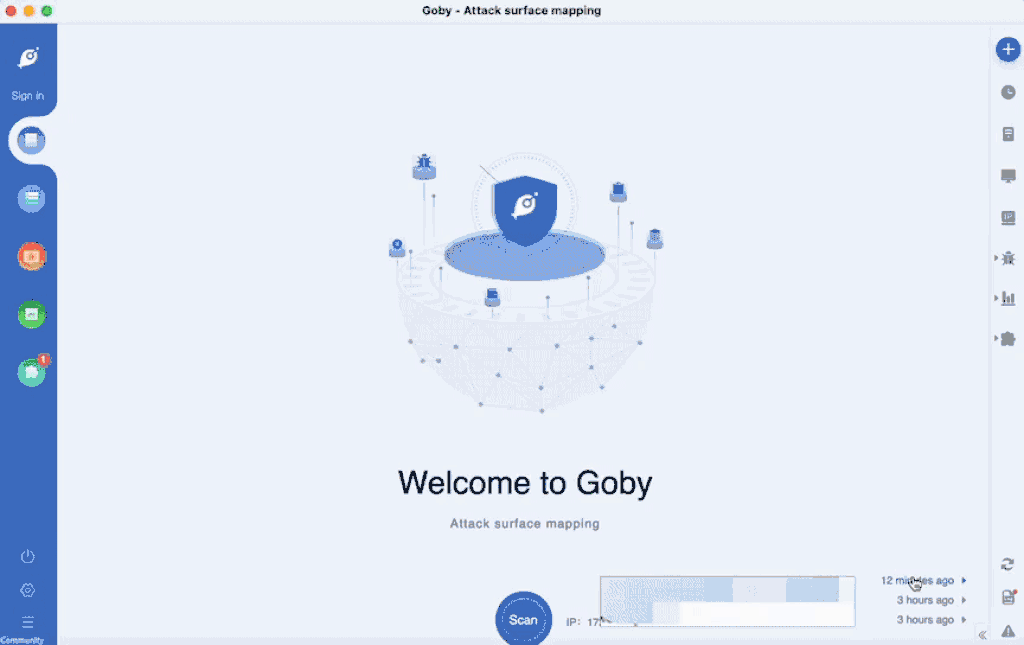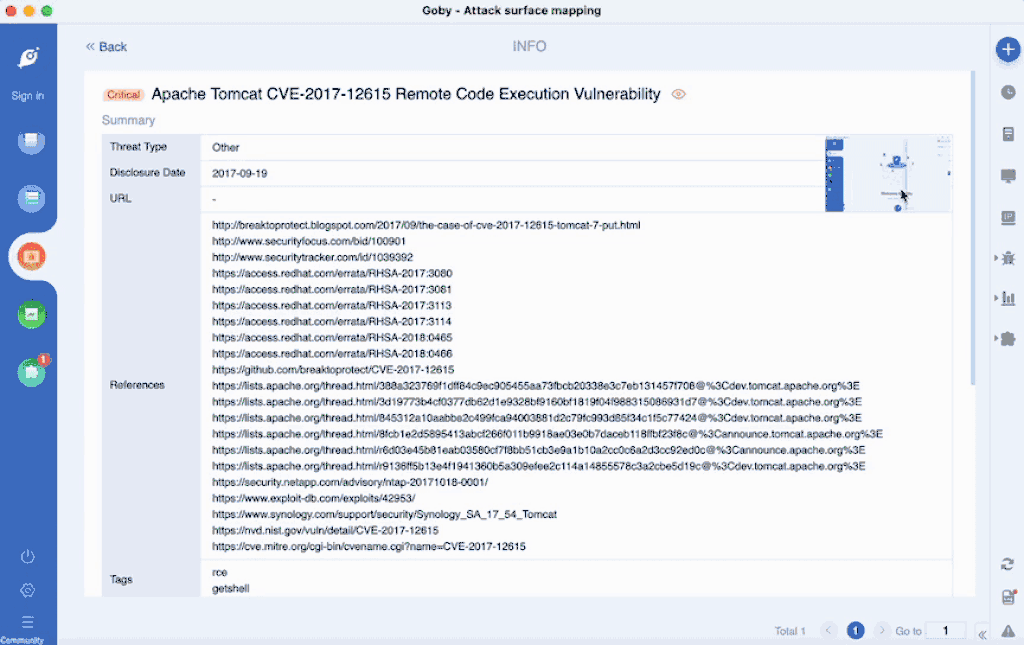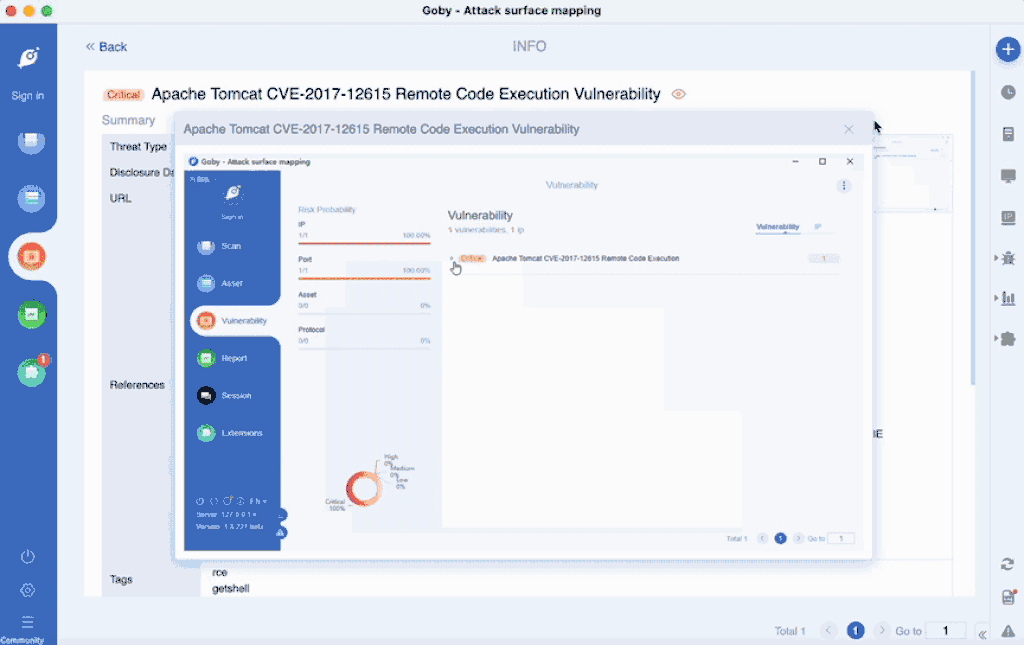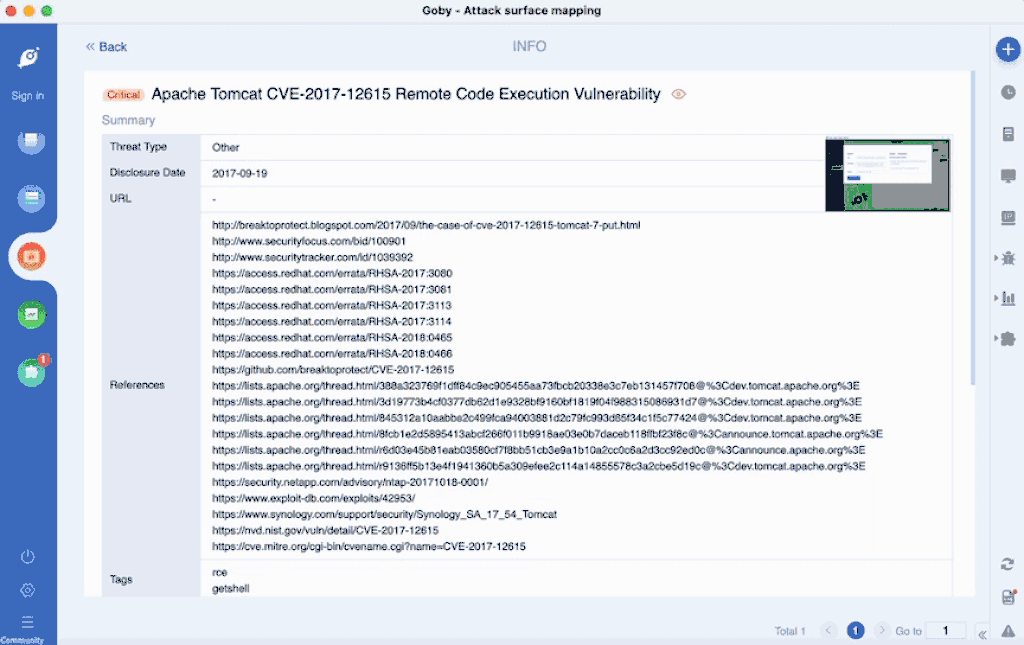
- Vulnerability module added a function to generate deserialization Payload, through the memory shell injection process
- Five Java deserialization vulnerabilities were added, including
- Bonitasoft Platform serverAPI Deserialization Vulnerability
- Liferay Portal Unauthenticated 7.2.1 C3P0 Deserialization Vulnerability (CVE-2020-7961)
- ManageEngine OpManager Deserialization Vulnerability (CVE-2020-28653)
- Zkteco Shiro Deserialization Vulnerability
- ZOHO ManageEngine Password Manager Pro Deserialization Vulnerability
- Fixed the problem that the environment variable http_proxy caused Goby to report errors abnormally
- Goby can now be updated online and vulnerabilities can be updated even if Goby is not in the Mac system Application directory
- Fixed the problem of occasional white horizontal lines in Goby
- remove network error report
Red team/Enterprise version update content
- All update content of 2.2.0 community version
- 20 new deserialization vulnerabilities were added, including
- Apache OFBiz xmlrpc Deserialization Vulnerability (CVE-2020-9496)
- Apereo CAS Before 4.1.7 Deserialization Vulnerability
- Dreamer CMS Shiro Deserialization Vulnerability
- EasyReport Shiro Deserialization Vulnerability
- FEBS Shiro Deserialization Vulnerability
- FH Admin Shiro Deserialization Vulnerability
- FineReport V10 Deserialization RCE Vulnerability
- ForgeRock AM Deserialization Vulnerability (CVE-2021-35464)
- Guns Shiro Deserialization Vulnerability
- J2eeFAST Shiro Deserialization Vulnerability
- JavaWeb_Layui Shiro Deserialization Vulnerability
- Liferay Portal 6.1.1 CE GA2 CB Deserialization Vulnerability
- MCMS Shiro Deserialization Vulnerability (CVE-2022-22928)
- OneBlog Shiro Deserialization Vulnerability
- pb-cms Shiro Deserialization Vulnerability
- QVIS-NVR Camera Management System RCE (CVE-2021-41419)
- RuoYi-plus Shiro Deserialization Vulnerability
- TIMO Shiro Deserialization Vulnerability
- Ysk ERP Shiro Deserialization Vulnerability
Zkteco Shiro Deserialization Vulnerability

Apache OFBiz xmlrpc Deserialization Vulnerability (CVE-2020-9496)

Beta1.9.325
2 years agoIn this update
• Add FID: Web feature data to cluster the same assets and quickly locate the original non feature assets
• New ip: port scanning format
• New extension scoring and sorting
• New 2022 dynamic theme
• Optimize the time when tip delay occurs
• Optimize the process of error reporting guidance and solution
• Optimize the format of developer mode printing information
• Add some fingerprint data
• The scan log keeps the last 10 log files
• When the mouse hovers over the asset, the corresponding port number can be displayed
• Solve the right sidebar style masking problem
• Solve the problem that novice guidance cannot skip
• Solve the problem that clicking on the histogram of the asset page is Chinese search
• Resolve duplicate Export Report vulnerabilities
• Solve the problem of service interruption parsing empty gzip response body and reporting errors
FID
ip: port scanning format
New extension scoring and sorting
New 2022 dynamic theme
Beta1.9.310
2 years agoIn this update
• Add new function IP library: Goby IP library is a graphical asset collection tool that expands with dots, designed to improve the breadth and accuracy of asset collection. Enter the target to start, and gradually expand the line to automatically discover and collect target assets.
• Add new webshell management function: You need to download the ShellHub plug-in first, and you can click the open shell button to pop up the webshell management interface, and you can directly operate the webshell.
• Add 18 UDP protocol analysis such as mdns, wdbrpc, etc.
• Add support for automatic update
• IP library newly supports one-click import ip/domain function
• IP library newly supports for clearing data
• Modify the IP library page caching strategy
• A single plug-in supports multiple minimized windows
• Support viewing other plugins of the same author
• Mac icon modification
• Fixed the upgrade failure due to spaces in the path under Window
• Mac upgrade script modification
• Fixed the data cache of scan configuration
• Fix the problem that scanning cannot be started normally after using the plug-in
• Solve the problem of multiple p tags in the updated content
Webshell management function-ShellHub extension
Two-year anniversary theme
IP Library

Webshell management function-ShellHub extension

Automatic update
Two-year anniversary theme
Beta1.9.320
2 years agoIn this update
• Proxy global state switching
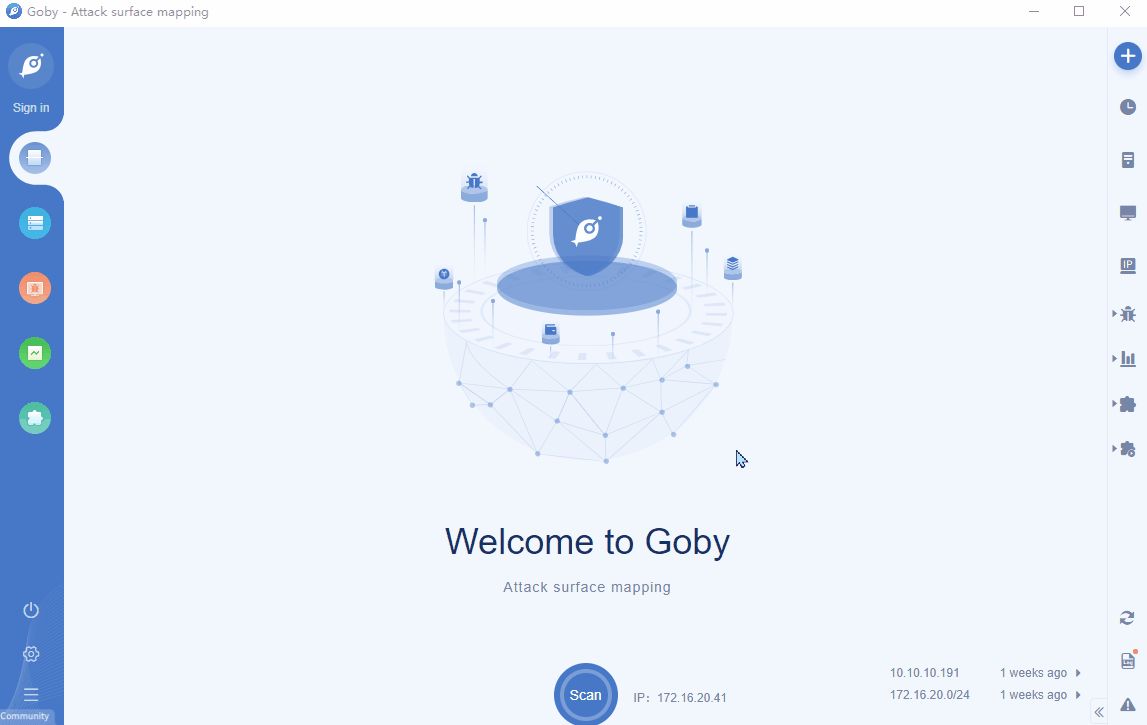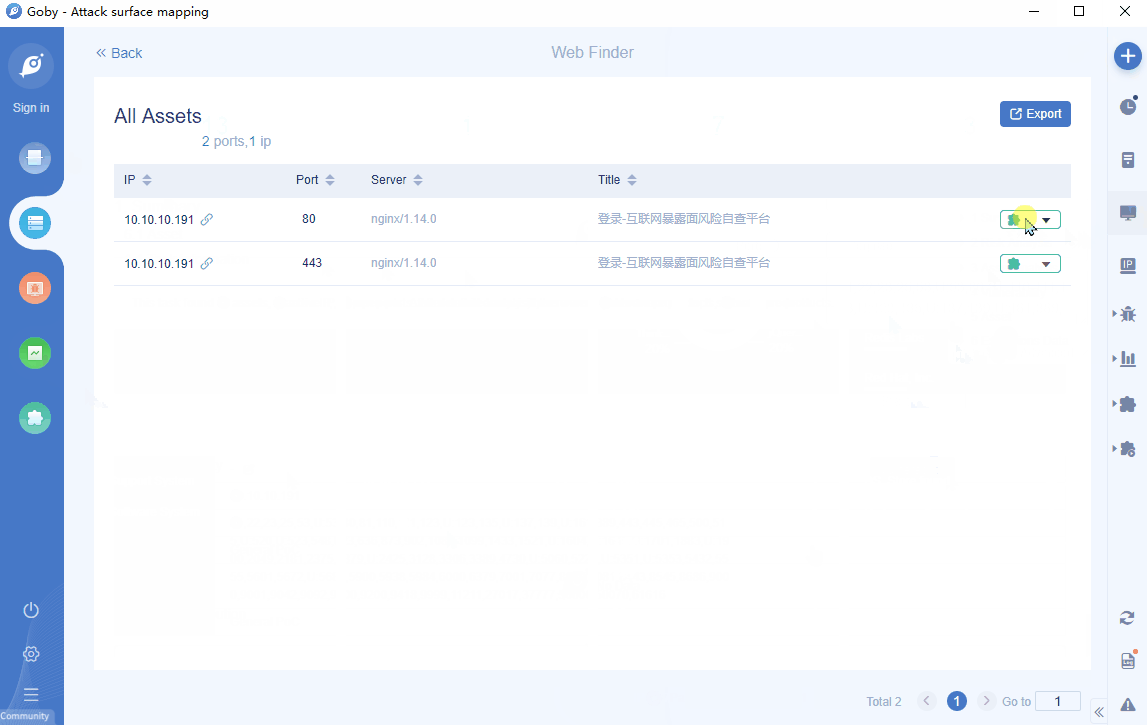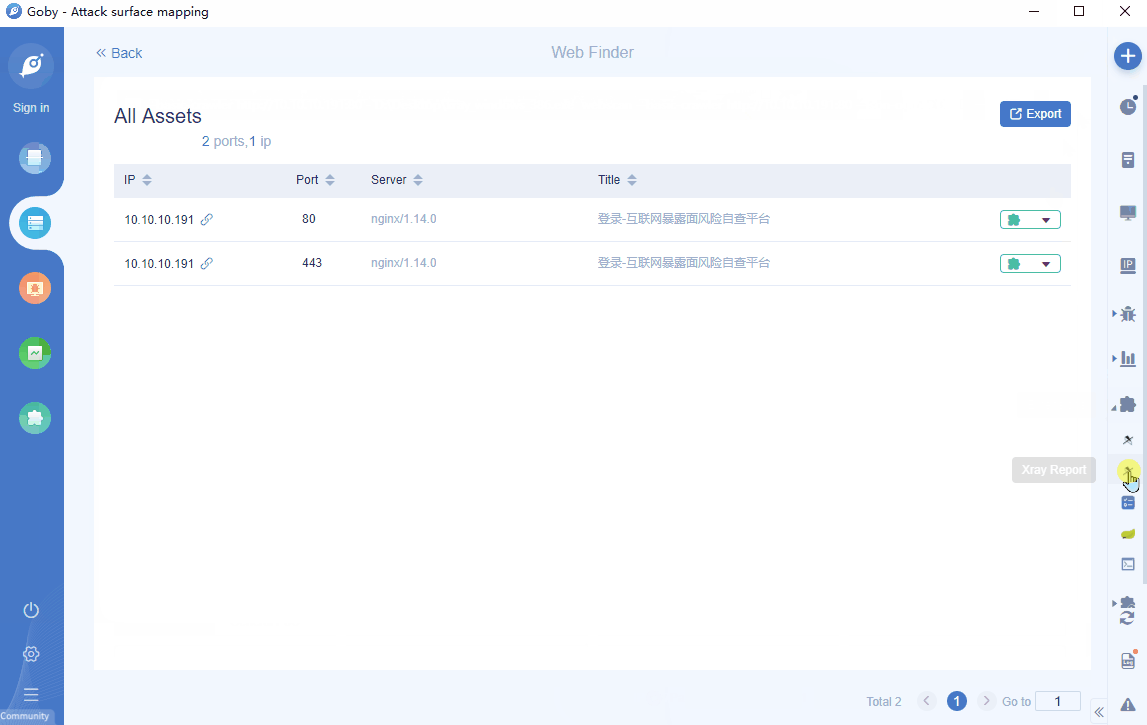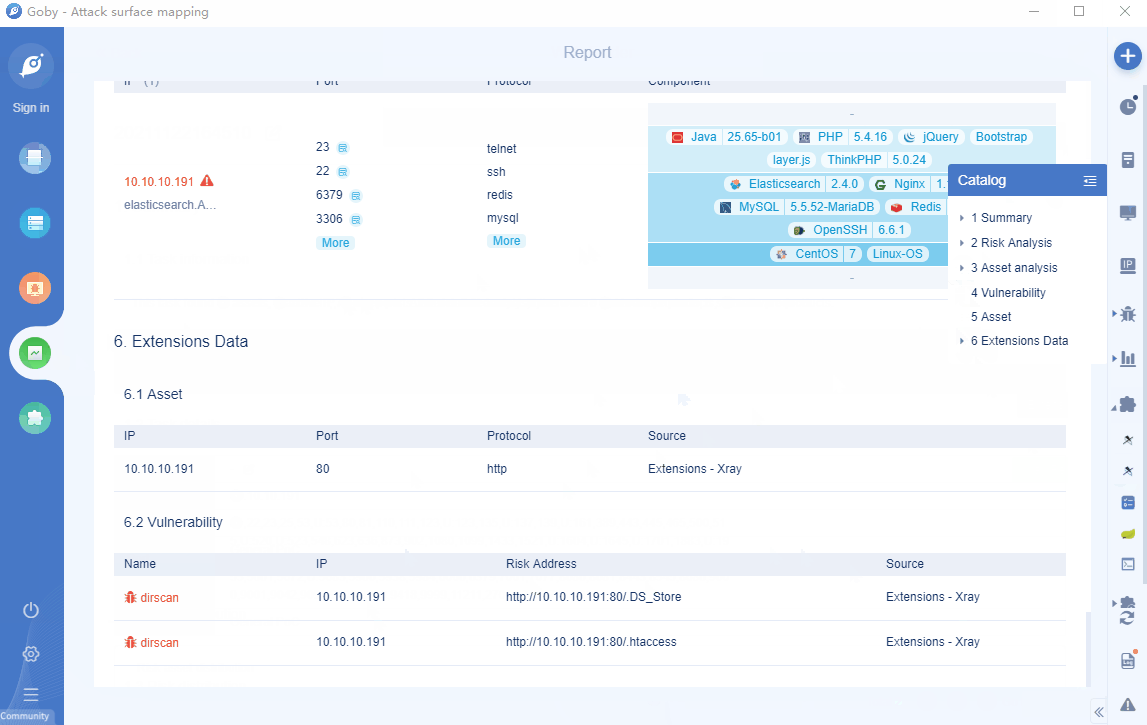
• The report supports extension data display
• Add 47 kinds of UDP protocol support
• IP library optimization update
• Mac version replaces some HD icons
• A single extension supports multiple minimized windows
• Optimize data cache for scan configuration
• Optimize the network prompt method for requesting the extension list when entering the application
• New extension minimization API
• Add extension operation server configuration API
• Solve the problem that there are more p tags on the updated content page
• Fix the problem that the automatic deletion of the upgrade package does not take effect after the Mac version upgrade
• Solve the problem that the value of HTTP header content length does not correspond to the amount of post data
• Solve the problem that scanning cannot be started normally after using the extension
Proxy global state switching
The report supports extension data display
IP library optimization update
Beta1.8.302
2 years agoIn this update
• Brand new EXP editor: add Exploit Test Tab for EXP writing. Add Variable Setting selection box in Scan Test page for http request setting
• Video Demo for dnslog with json-format exploit
• Video Demo for reverse shell with json-format exploit
• Exploit preview: showing exploit step and effect for a specified exploit
• Customized exploit group: select exploits and add those in a group, select your customized group when scan, that will only scan with those exploits in group
• More exploits
• Support plugin window minimization
• Add vulnerability detail in report
• Optimize service interruption - can not scan with current network interface card
• Optimize service interruption - scan format error
• Fix bug about showing last scan ip in current scanning result
• Fix bug about EXP preview
• Fix bug about customized explot group
• Update setting page UI
• Optimize scanning animation when not perform vulnerability scanning
• Optimize expansion and collapse UI in function navigation bar
• Fix cannot scan port range
• Fix cannot use customized dict when vnc bruteforce
Brand new EXP editor
Video Demo for dnslog with json-format exploit
• Video Demo for reverse shell with json-format exploit
Exploit preview
Customized exploit group
Beta1.8.298
2 years agoIn this update
• Fix newly discovered XSS security issues; it is recommended to update the Http plug-in to the latest version
• Add batch export of historical tasks
• Optimize webfinder title sorting problem
• Fix the occasional issue that port 9100 is not disabled
• Restrictions that do not support scanning ipv6 addresses
• Provide the default name of the custom port group
• Modification of blank error report if not connected to external network
• Optimize mac toolbar icons
• Import the icon when importing tasks
• Optimize other styles, copywriting, and interaction issues
Beta1.8.294
2 years agoIn this update
• Fix xss security issues
Beta1.8.293
2 years agoIn this update
• Added 40 combat vulnerabilities: including Cisco HyperFlex HX storfs-asup remote command execution vulnerability (CVE-2021-1497); VMware vCenter Server remote code execution vulnerability (CVE-2021-21985); Inspur ClusterEngine remote command execution vulnerability; Weaver ecology Any file upload; UFIDA NC arbitrary code execution, etc., have been verified in actual combat, and are available for study, research and discussion.
• Add the option of not scanning network printers: filter out port 9100 to prevent network printers from working incorrectly.
• Added background scan: when exiting Goby, a pop-up box reminds that a task is being executed and asks whether to continue exiting Goby.
• Report support to export website screenshots: Export all data including assets, vulnerabilities, reports, website screenshots and icons.
• Plug-in label display: newly launched plug-ins, put them on the top for one week, add the "new" label.
• Add scan status.
• The nation flag icon is added to the language list.
• The new PoC management feature, users can open the storage location of the local PoC.
• Temporarily disable the scan to IPv6 function.
• Fix the problem that when input PoC file name press Enter to trigger a restart.
• Fix the problem that the import PoC prompt is always being imported.
• Fix the problem that the network card does not restart the service after an error is reported.
• Fix the problem that the second export of the task pop-up window is incomplete.
• Fix the problem that WebFinder cannot export all.
• The error logic of pcap not finding the network card is restored to a prompt that the network card cannot be scanned.
• Fix too many assets report cannot be loaded.
• Fix the incomplete export of excel table.
• fix other styles, copywriting, and interaction issues.
New vulnerabilities
Demos: https://github.com/gobysec/GobyVuls

pngoption of not scanning network printers

background scan

Report support to export website screenshots

Beta1.8.279
2 years agoIn this update
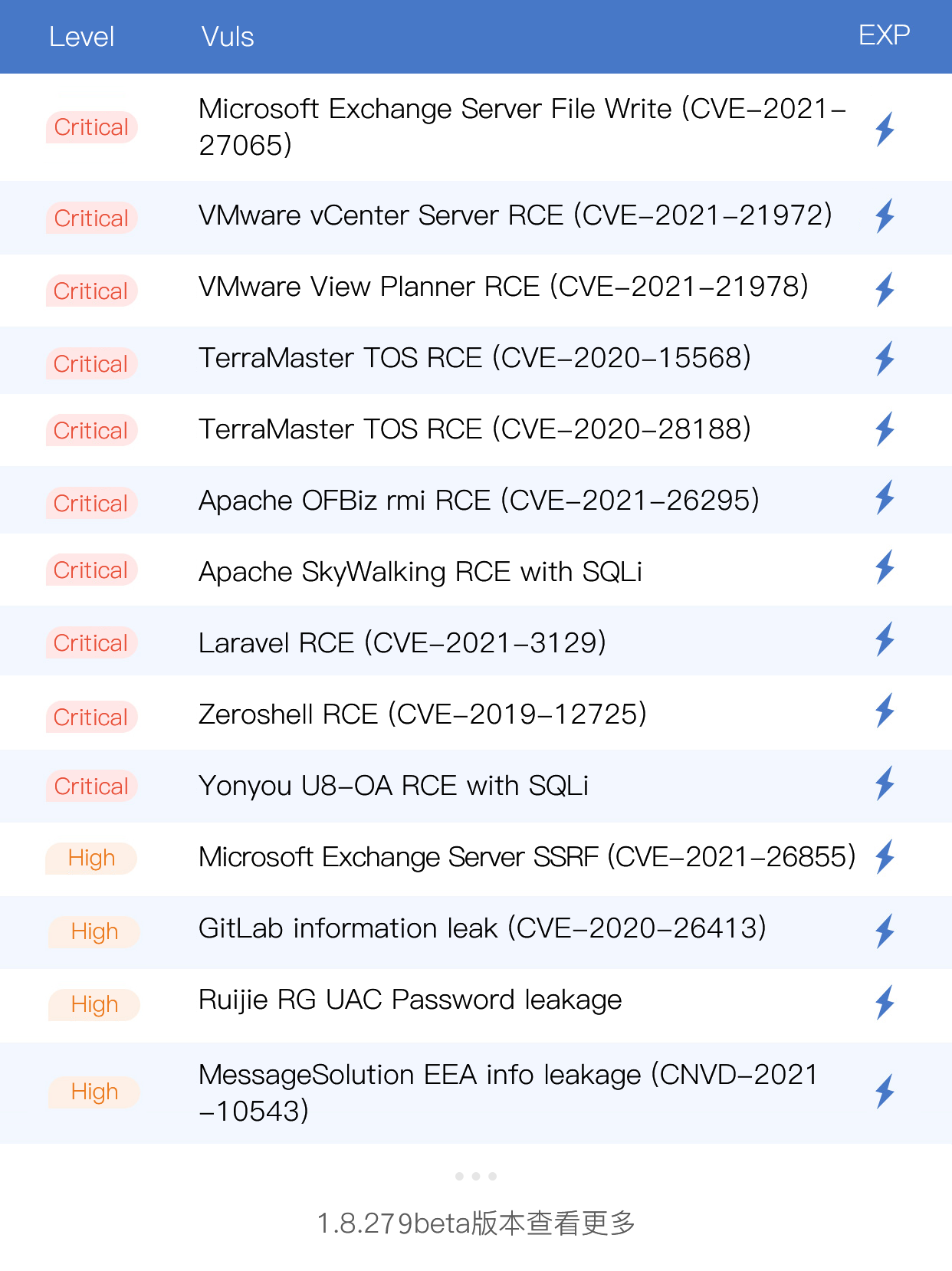
• 35 new vulnerabilities added:Microsoft Exchange Server File Write (CVE-2021-27065), Microsoft Exchange Server SSRF (CVE-2021-26855), VMware vCenter Server RCE (CVE-2021-21972) , etc. Almost all of them can work well, please enjoy.
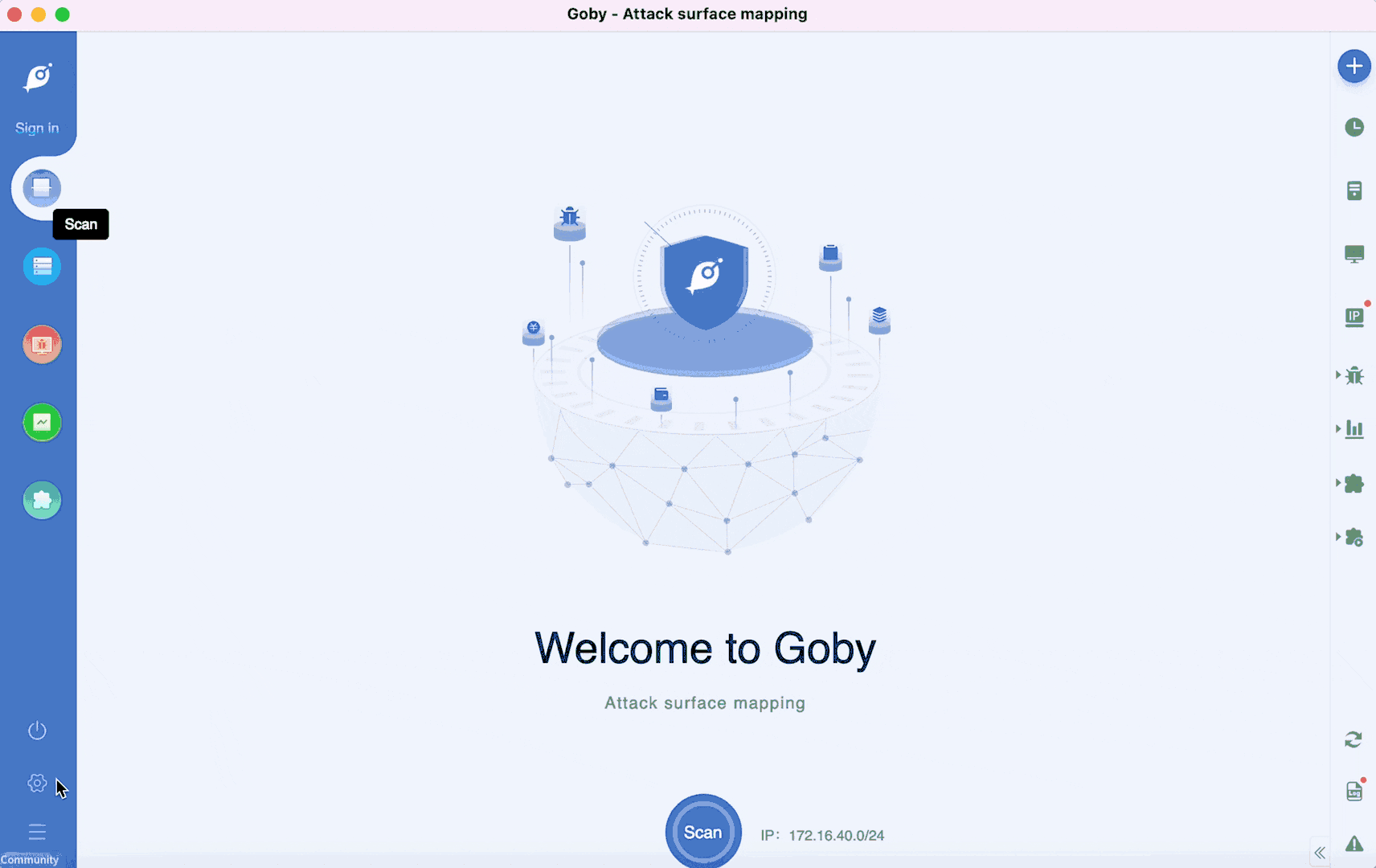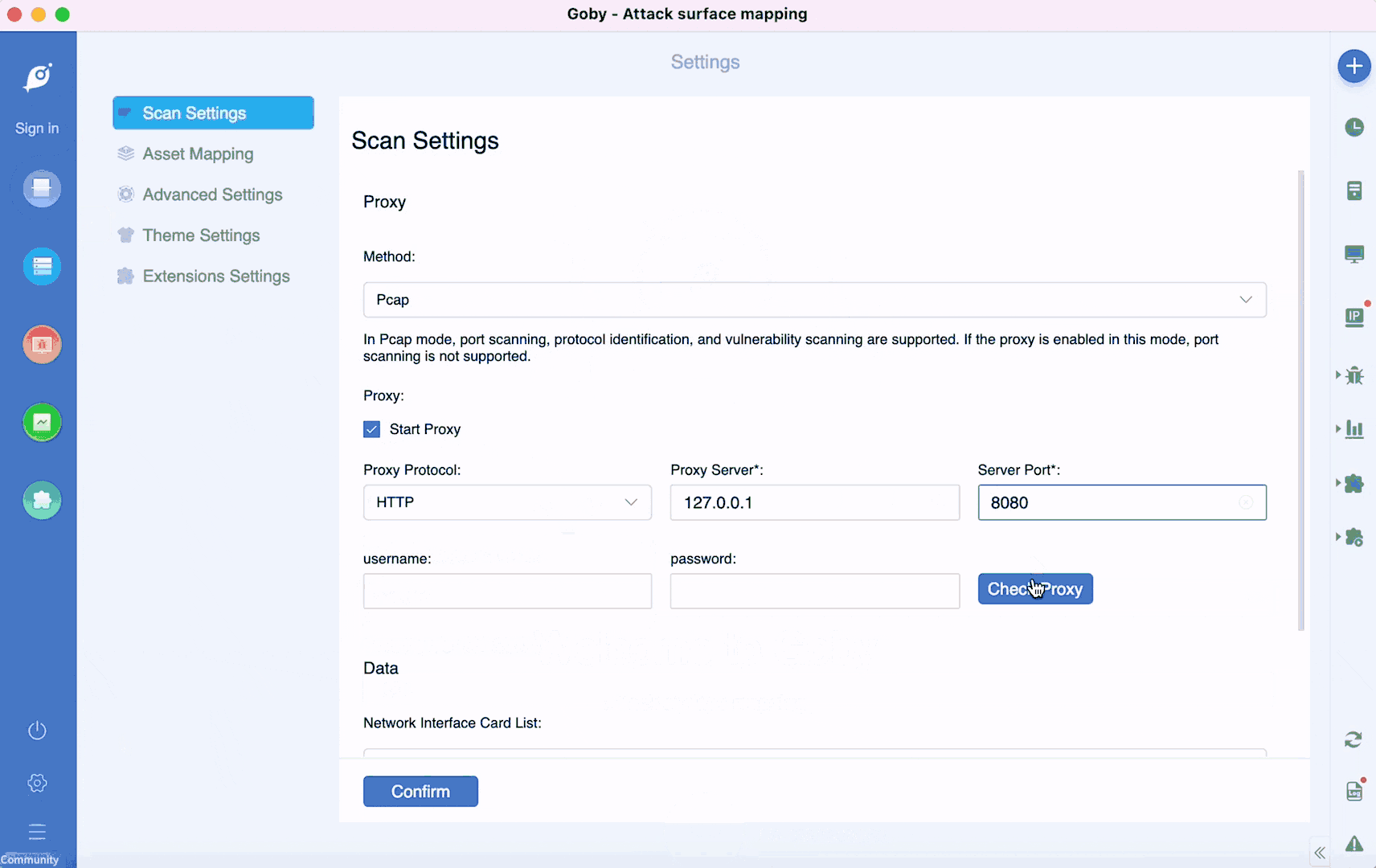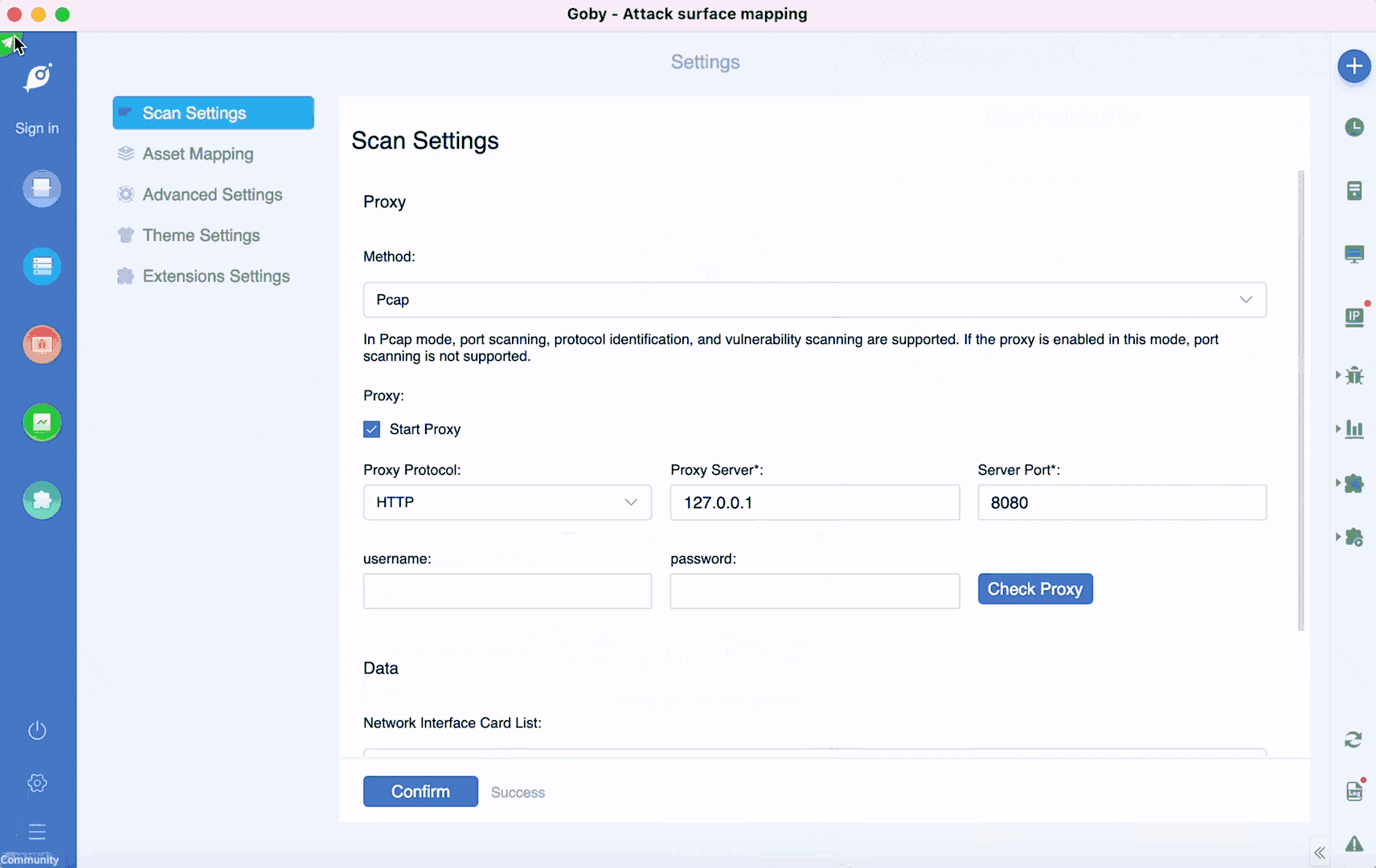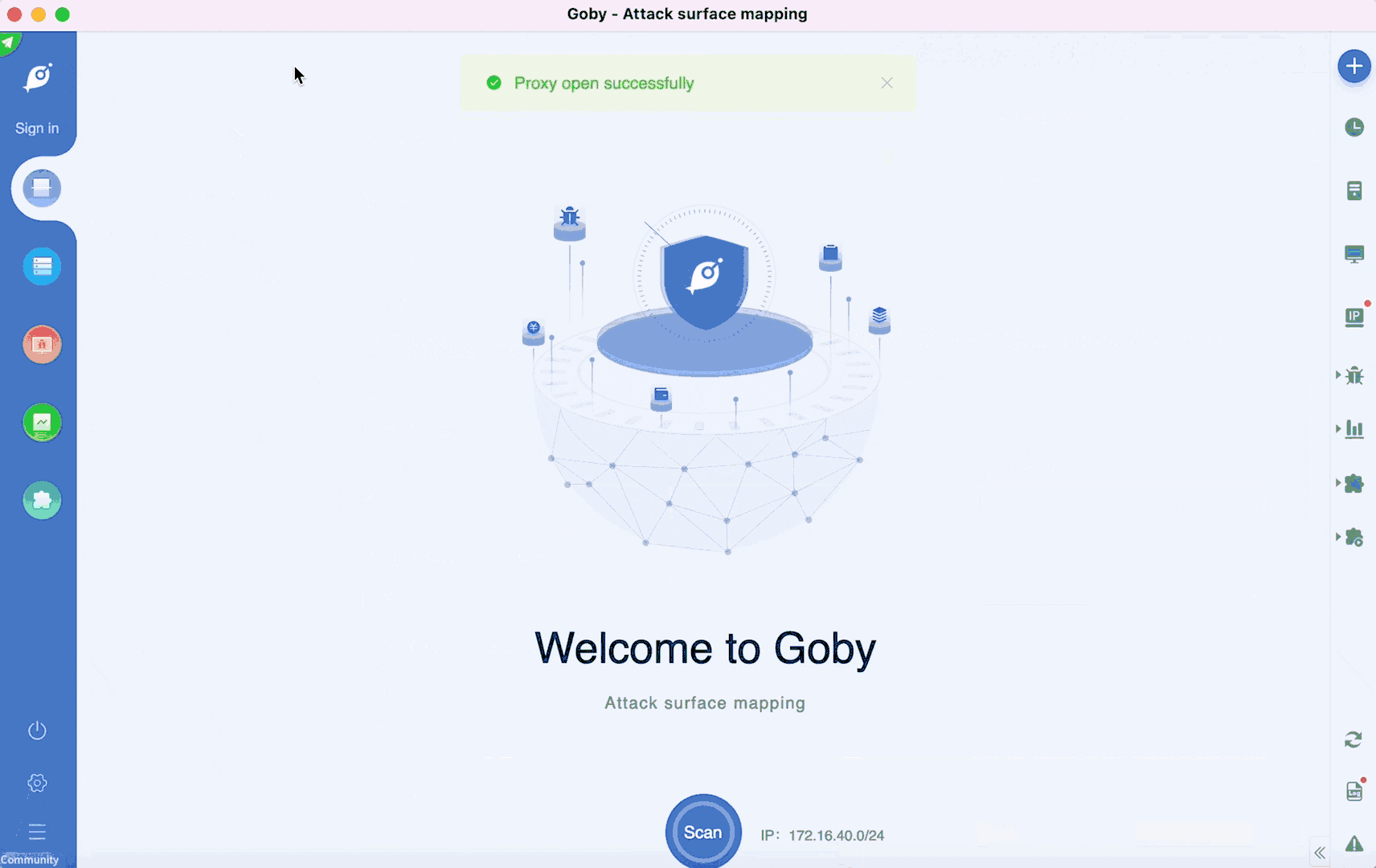
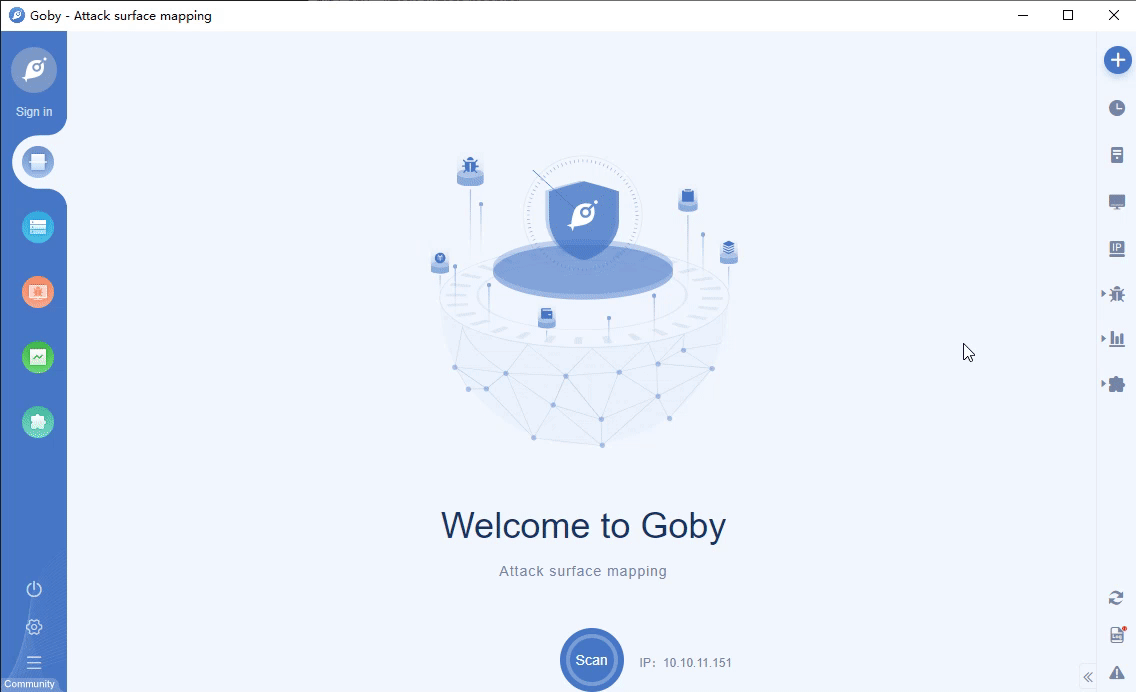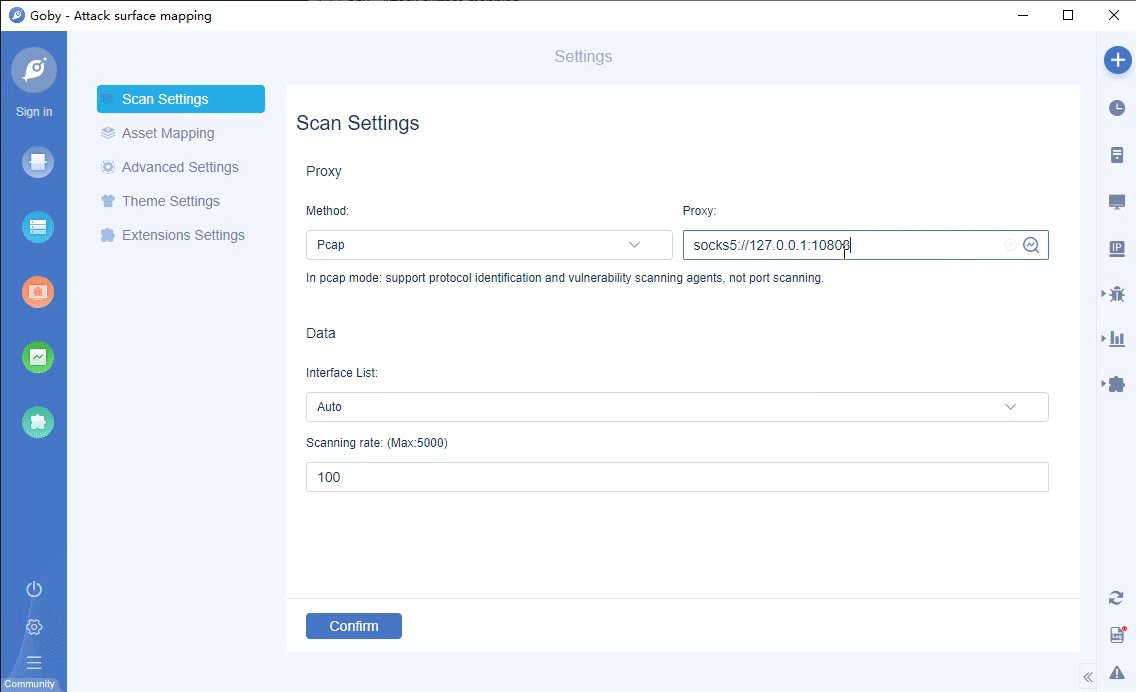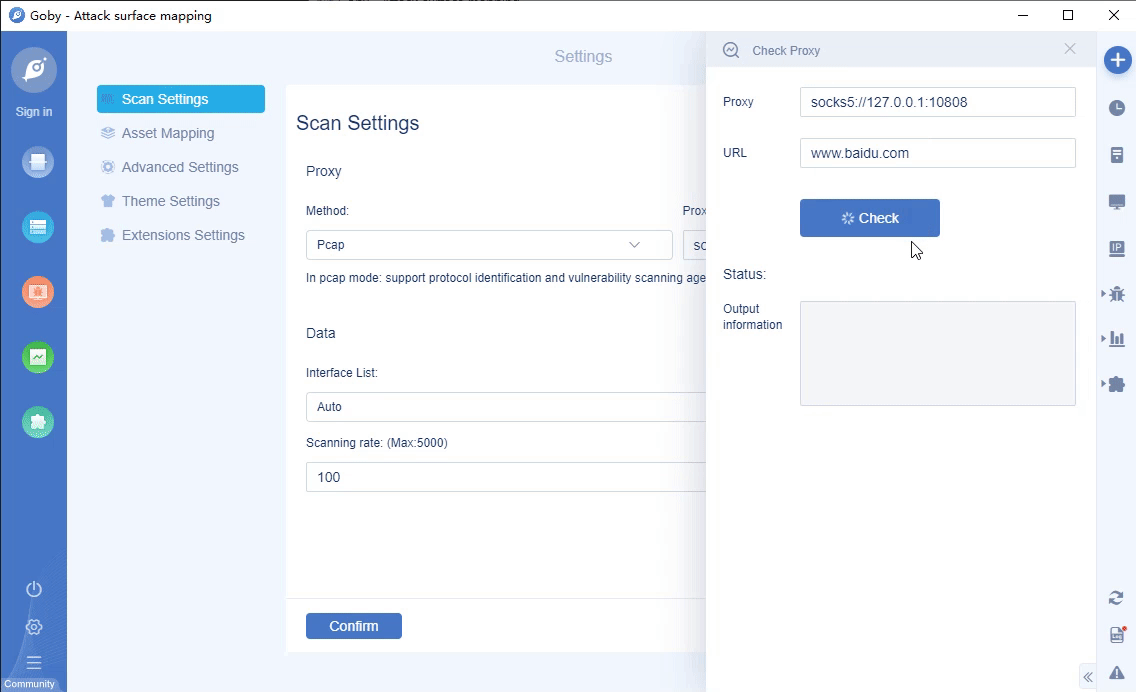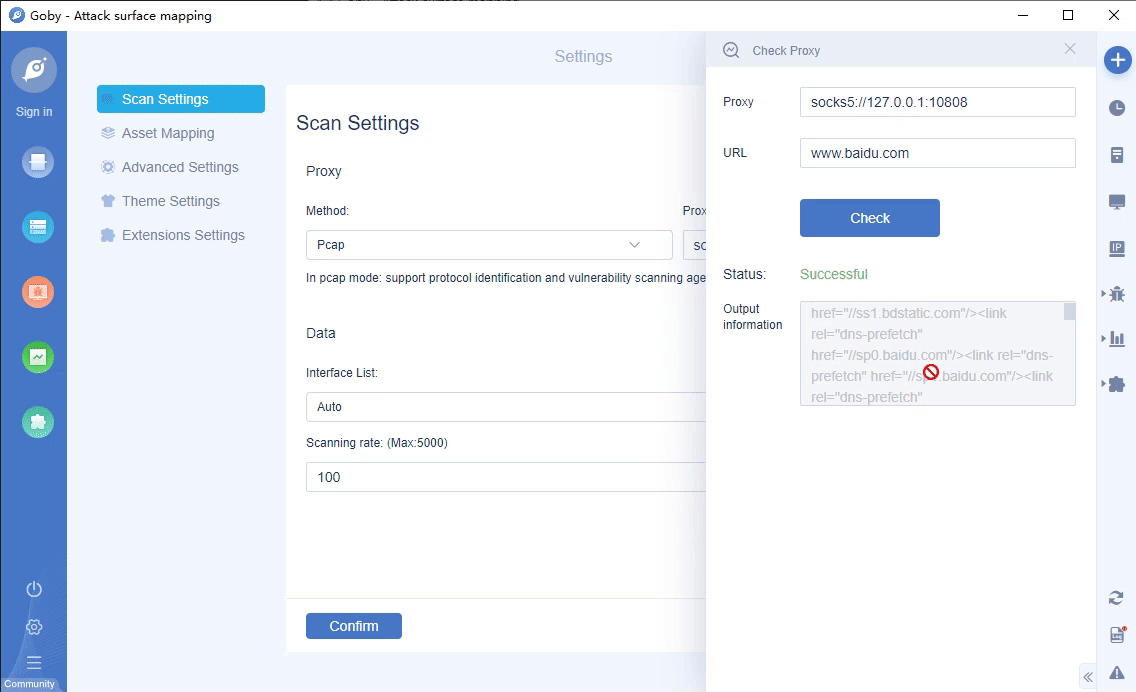
• New proxy detection function: fill in the proxy and test the URL address to detect whether the proxy is connected successfully.
• Newly added banned IP list: skip some IPs that do not need to be scanned to improve scanning efficiency.
• Add http, https proxy scanning.
• New log real-time output: view the latest log dynamics.
• When the remote service is interrupted, prompt to modify the remote service address pop-up window.
• Support that historical tasks can be edited and scanned again.
• Support IP replication in historical task.
• Optimize the interactive prompt for the exporting of PDF report.
• Optimize local service interruption error reporting.
• Optimize some deeply hidden but frequently used functional interactions.
• Fixed several service interruption and crash issues.
• Fix the issue of scanning https for single IP in PoC list.
• Fixed the problem that the vulnerability banned scan still has vulnerability data.
New vulnerabilities
Demos: https://github.com/gobysec/GobyVuls
pngproxy detection function
banned IP list
http, https proxy
log real-time output
Beta1.8.275
2 years agoEXP Special Edition