Gobysec Goby Versions Save
Attack surface mapping
Beta1.8.239
3 years agoIn this update
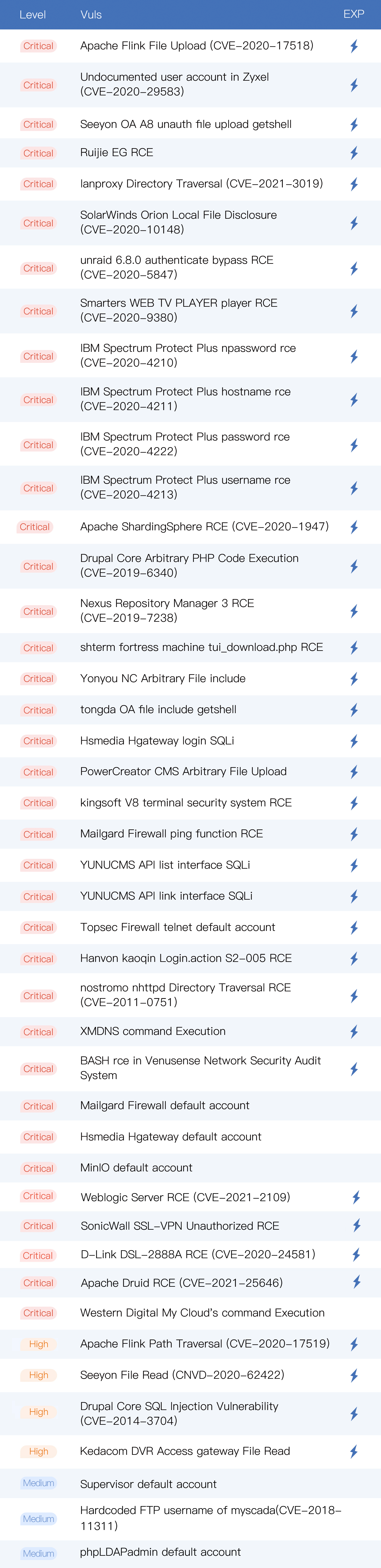
• A total of 44 new vulnerabilities: Weblogic Server RCE (CVE-2021-2109)、 Apache Flink Upload(CVE-2020-17518)、lanproxy Directory Traversal(CVE-2021-3019)、Ruijie EG RCE、Apache Druid RCE (CVE-2021-25646), etc;
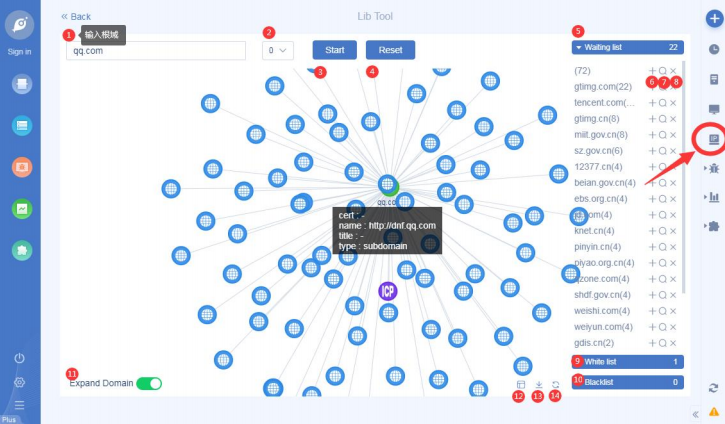
• Add IP library: flip chart combat! Through the root domain, quickly define a target network asset map;
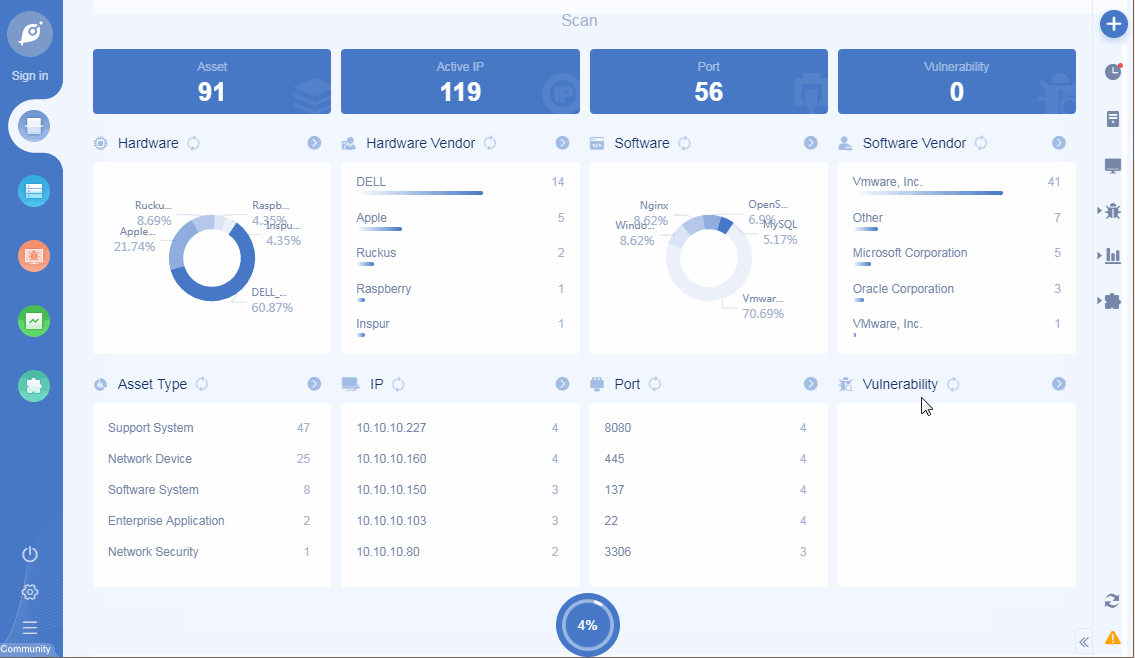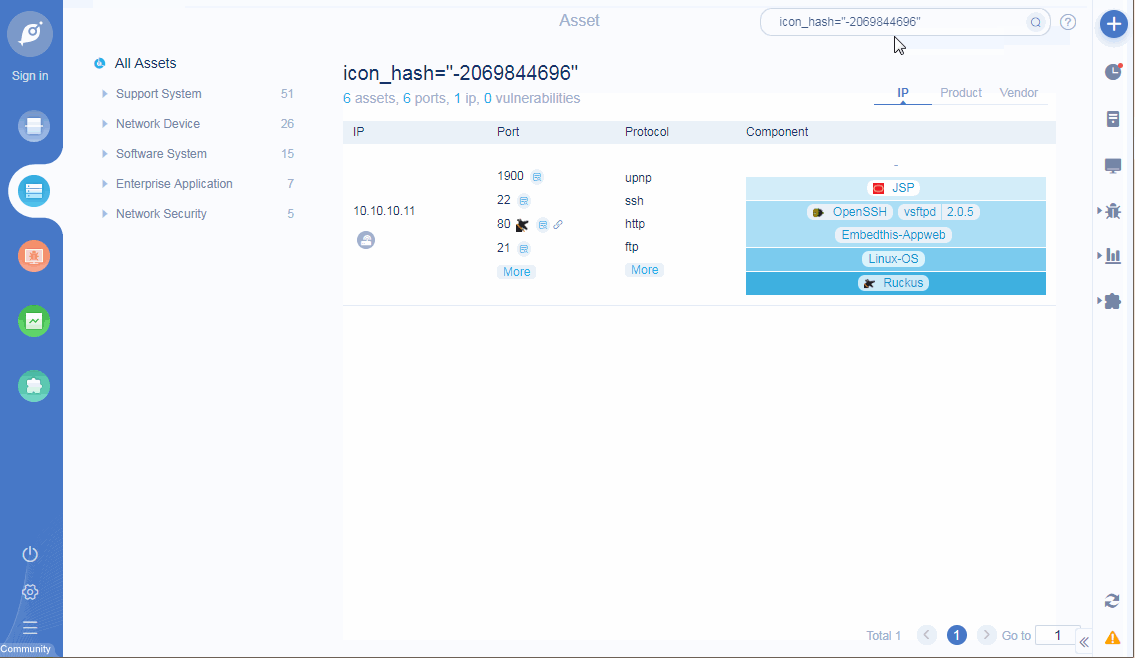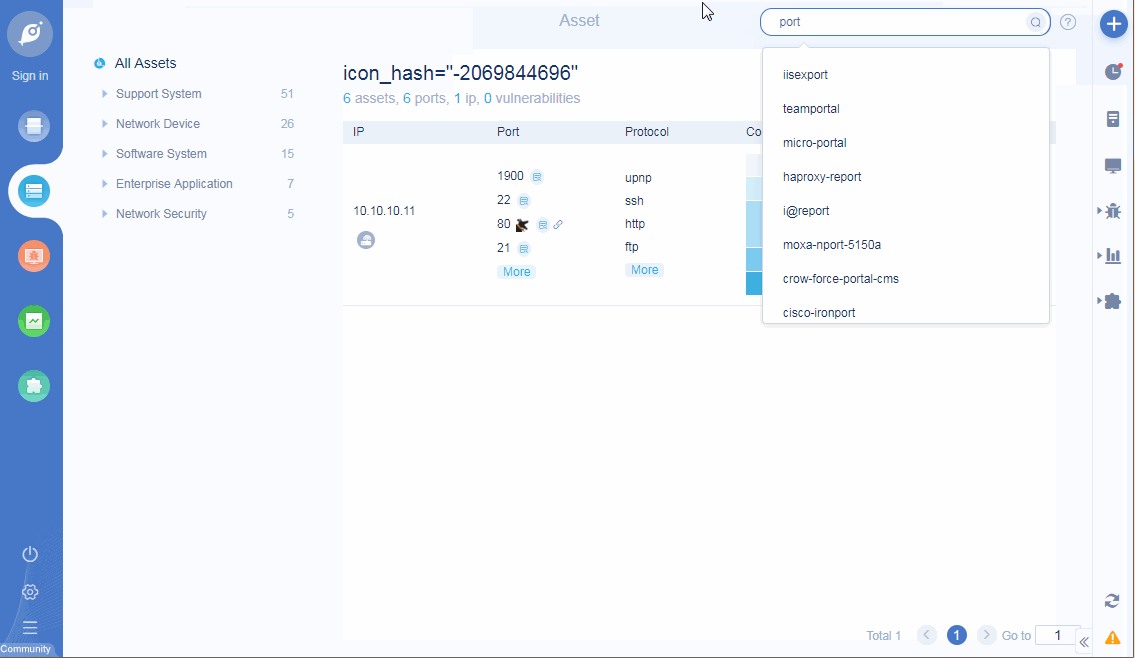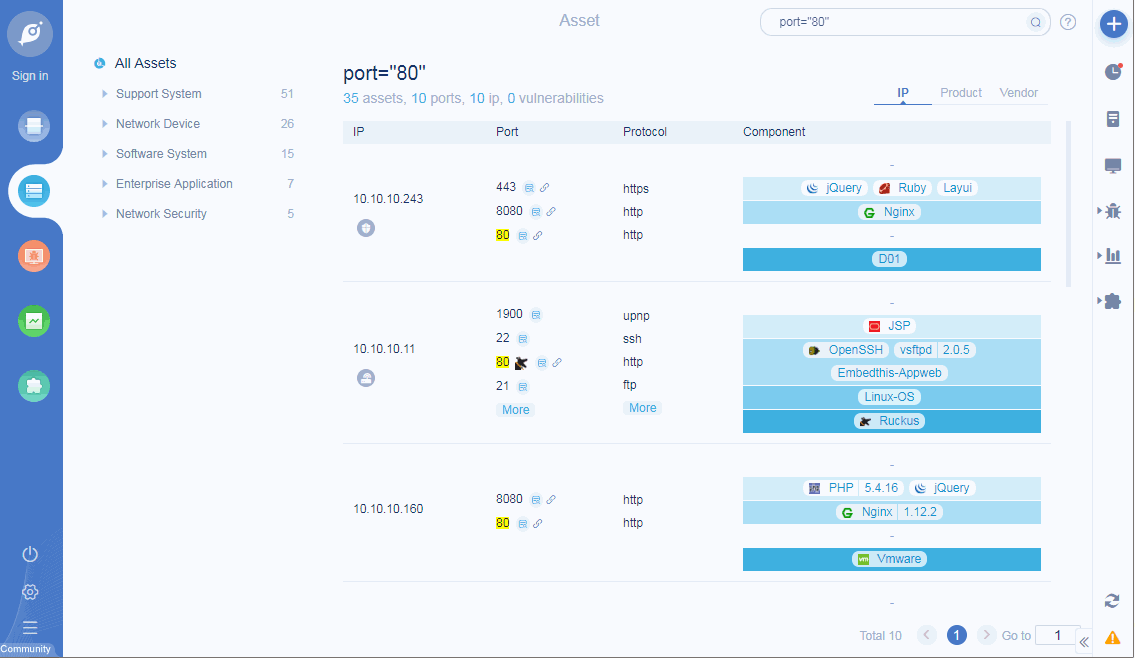
• Add ICON mapping function: support query rules to search current task assets, such as query ip, port, app, protocol, title, etc;
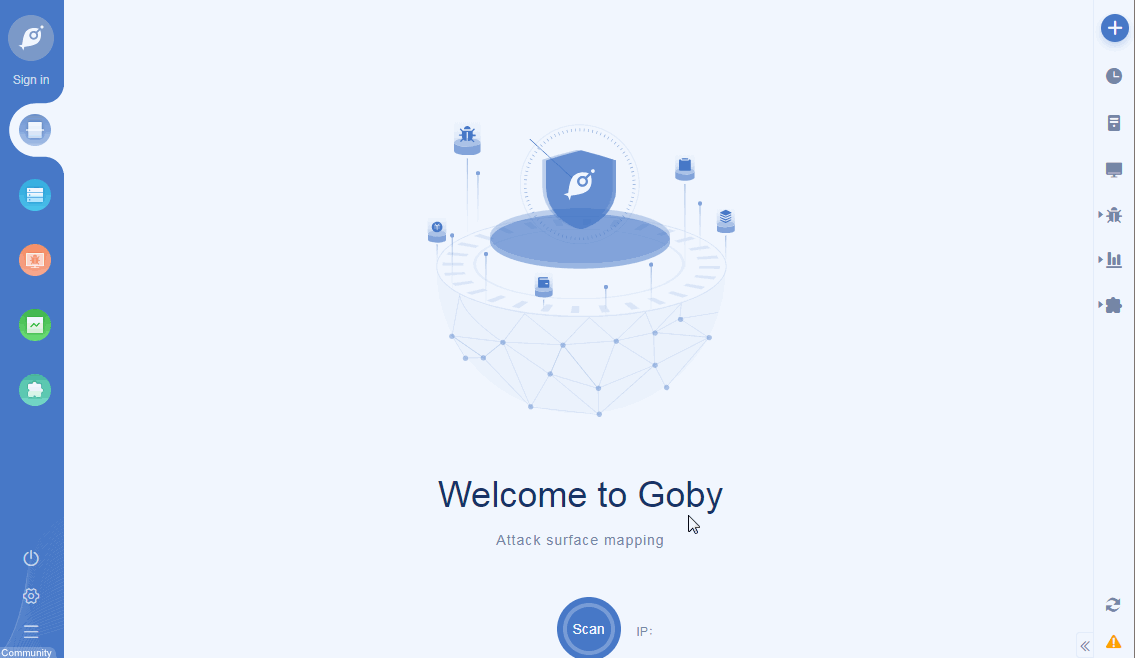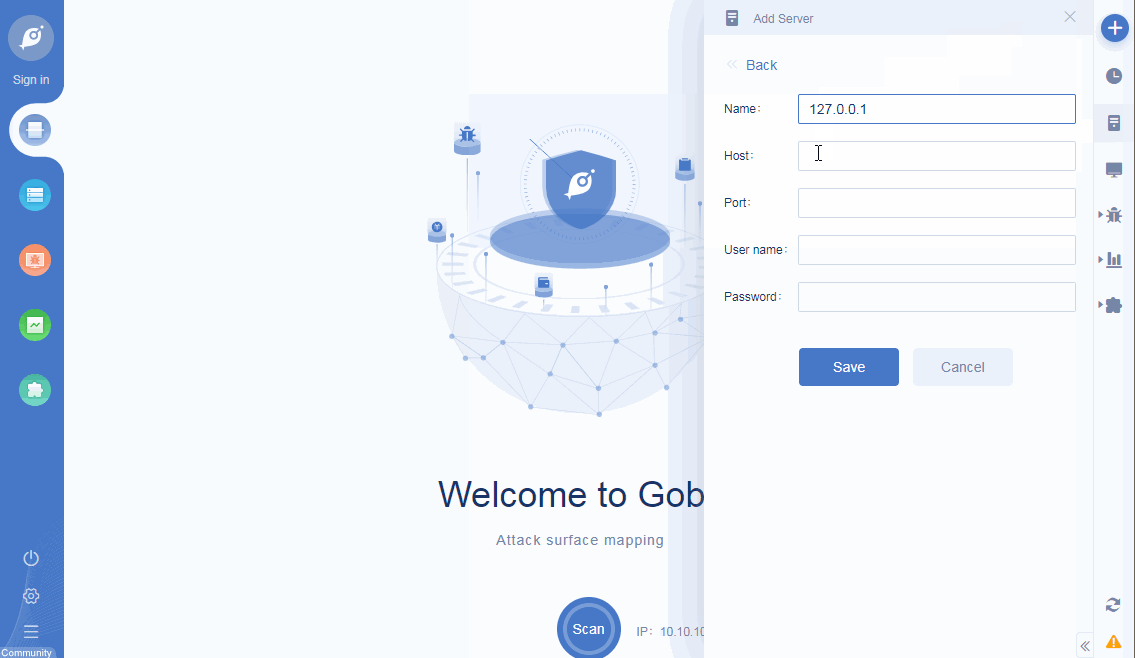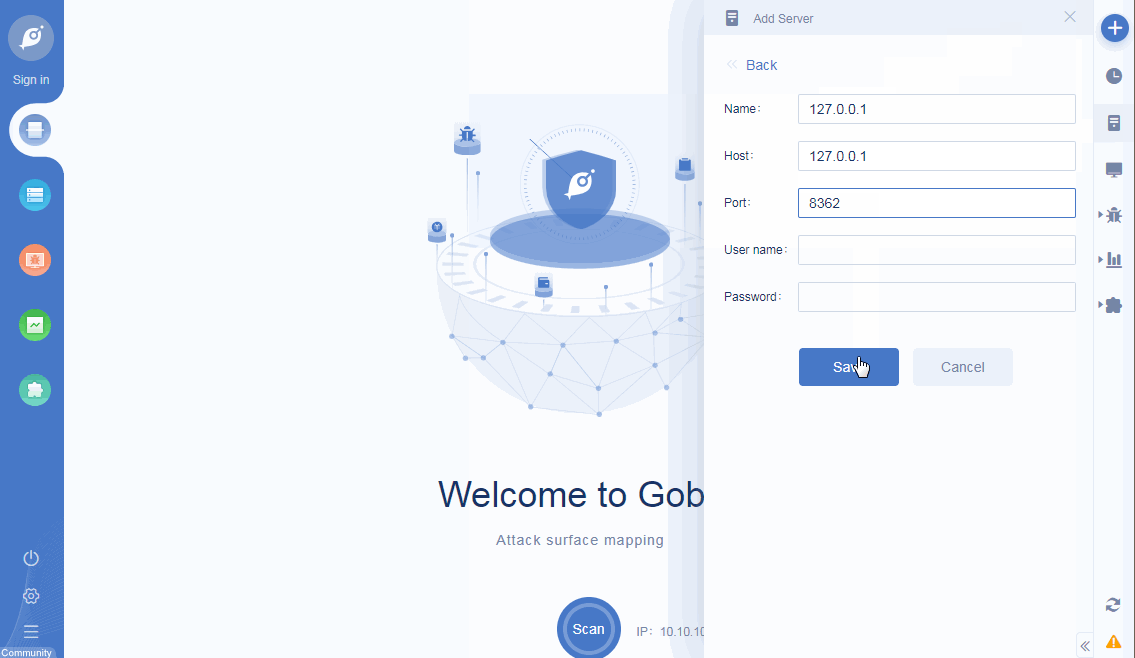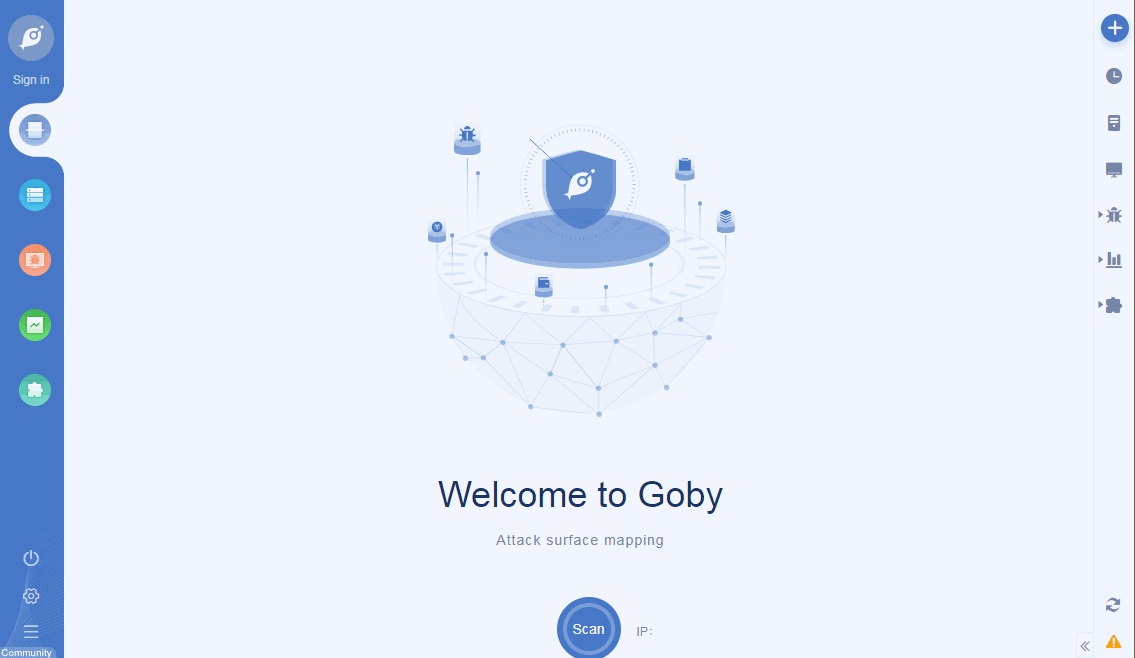
• New server management: support for adding multiple remote servers, and support for server management;
• Add support for windows 32-bit, mips and arm versions: currently limited to command line startup, the startup method is the same as windows 64-bit, run goby-cmd:
./goby-cmd -apiauth user: pass -mode api -bind 0.0 .0.0:8361
• New protocols: asterisk,barracuda-bcp,beacon ccnet,ceph,daap,firebird,nomachine-nx,remoting,rtmp,stun,svrloc,varnish-cli, etc;
• New extensions: weak password dictionary: DictionaryConfig, timing task function : Task Queue, etc;
• Support specifying multiple poc for scanning;
• Fix online upgrade issues;
• Optimize the coding display of exploits;
• fix some mistake of pocs;
• Fix the issue of white screen caused by Chinese themes;
• Fix the problem that website screenshots cannot be displayed;
• Optimize partly hidden deep but frequently used functional interactions;
New vulnerabilities
Demos: https://github.com/gobysec/GobyVuls
Flip chart operations
ICON mapping
server management
SendMail
Beta1.8.230
3 years agoIn this update
• A total of 22 new vulnerabilities: Yonyou NC RCE, SaltStack RCE (CVE-2020-16846) , Citrix XenMobile Arbitrary file read (CVE-2020-8209)(2020-11-16), Apache Unomi RCE (CVE-2020-13942), vBulletin SQLi (CVE-2020-12720), Apache NiFi Api RCE, etc. • Added RDP bruteforce, and support to extract desktop screenshots from RDP; • Added toolbar: The functions that can be operated globally and used frequently are uniformly placed -- toolbar, such as "New scan", is more convenient and direct; • New extension entry point: Support for the role of extensions in the scanning process, and develop two extensions - Task Queue and Database Asset as examples; • Support online upgrade version: when a new version appears, there is no need to re-download the complete installation package, you can directly upgrade the program internally, and retain historical data; • Added four new honey pot fingerprints; • When the port is occupied, it can be modified to another port; • Fixed some pages with no data return problem; • Fixed some inaccurately reported; • Fixed some crash issues; • Fixed some display problems.
New vulnerabilities
Demos: https://github.com/gobysec/GobyVuls

RDP Bruteforce

The toolbar

Task Queue

Change occupied port

Beta1.8.221
3 years agoIn this update
• A total of 30 new vulnerabilities: CVE-2020-14882/CVE-2020-14750, CVE-2020-14883, XXL-JOB API Unauthenticated RCE, VMwareWeaver_e-Bridge_File_Read, Yonyou_GRP-U8_RCE,and crawler based vulnerabilities, such as Fastjson, Stucts2, etc. • New protocols of iot: added ddp, jt808/809, sl651. • New Cowrie honey pot identification, and two new honey pot fingerprints; • Added web crawler, and support crawled information to display. • Support to set the socket scan rate: default is 100. By reducing the scan rate, the scan crash can be improved. • New language support -- French, translated by @POC Sir. Thank you very much to this community contributor. • Vulnerability scanning automatically ignores honeypot assets. • Fixed false positives of IBM vulnerability. • Fixed CVE-2020-2551 inaccurately reported. • Fixed some crash issues. • Fixed some display problems.
New vulnerabilities

Web crawler

Fastjson 1.2.24 RCE

Crawled information

Set the socket scan rate

New language support -- French

Beta1.8.202
3 years agoIn this update
• A total of 22 new vulnerabilities: CVE-2020-1948, CNVD-2020-46552, CVE-2019-1652, CVE-2017-17215, CVE-2016-10134, etc. • New 100+ fingerprint rules. • New protocols: added corbaloc、edp、gbase, etc. • Added honeypot discovery: Currently, jSONP and keyword honeypots are supported, and low-interaction honeypots and high-interaction protocol honeypots will be added later. • New extension types: users can filter functions, themes, controls and other extensions to facilitate on-demand downloading. • The MSF extension supports browsing for file paths. • Opened the plug-in entry point at the Webfinder. • Custom PoC supports fuzzy matching query syntax, automatically matching to APP ="". • Extensions that are unzipped to directories can be removed through the GUI. • Optimized proxy server congestion and shutdown without error prompts. • Fixed CPU and memory usage problems. • Fixed false positives of Struts2 S2-046 vulnerability. • Fixed some issues of the Sockset agent pattern. • Fixed the problem of HTTPS vulnerability failure in some cases. • Fixed some display problems.
New vulnerabilities

Honeypot discovery

Beta1.7.194
3 years agoIn this update
• A total of 17 new vulnerabilities: CVE-2020-1948, CNVD-2020-46552, CVE-2019-1652, CVE-2017-17215, CVE-2016-10134, etc. • 200+ fingerprint rules. • Added type of theme extensions: users can develop themes by themself. • Support connection to remote service if local service cannot be started. • Support to copy the bounce shell. • Fixed to search for protocols issues. • Fixed CVE-2020-8515 inaccurately reported. • Fixed some display problems.
New vulnerabilities

Theme extensions:
Sources: https://github.com/gobysec/GobyExtension/tree/master/samples


Beta1.7.192
3 years agoIn this update
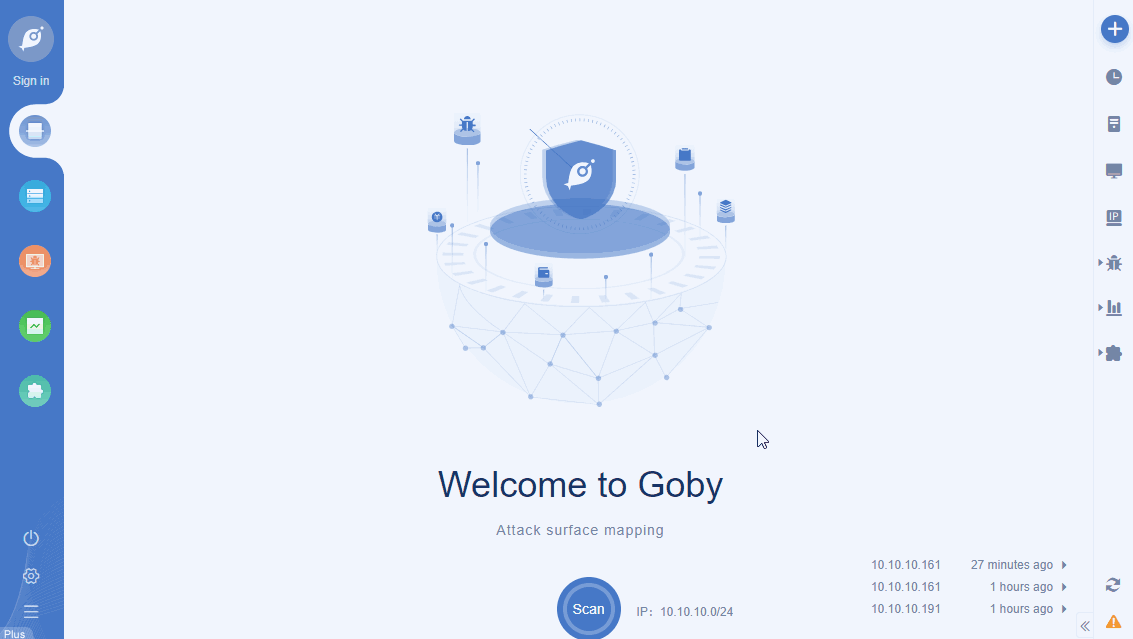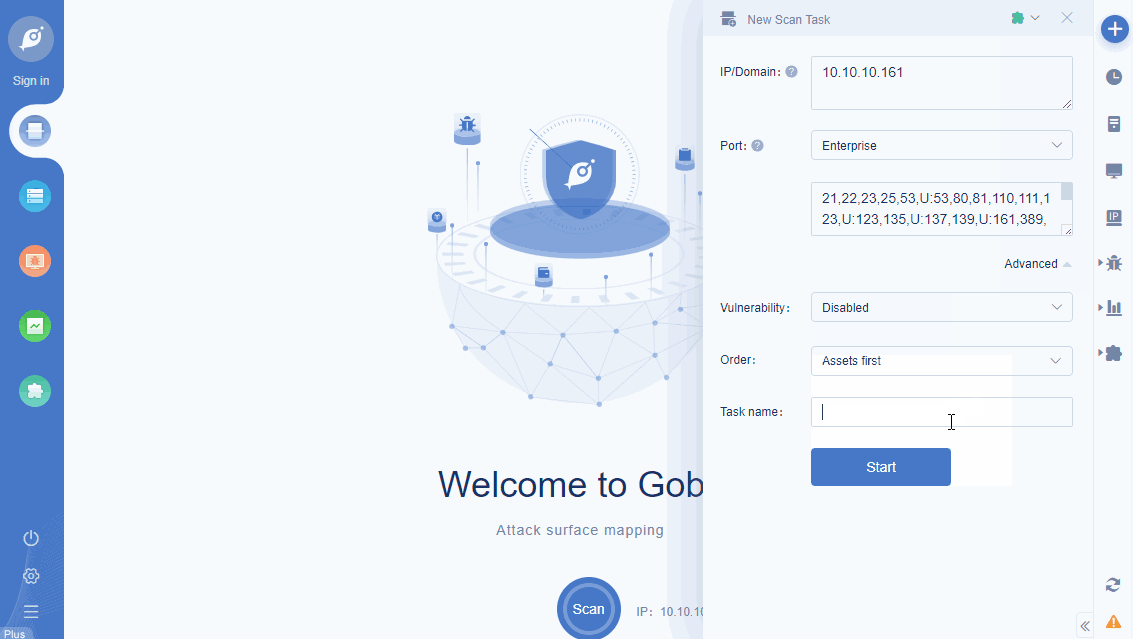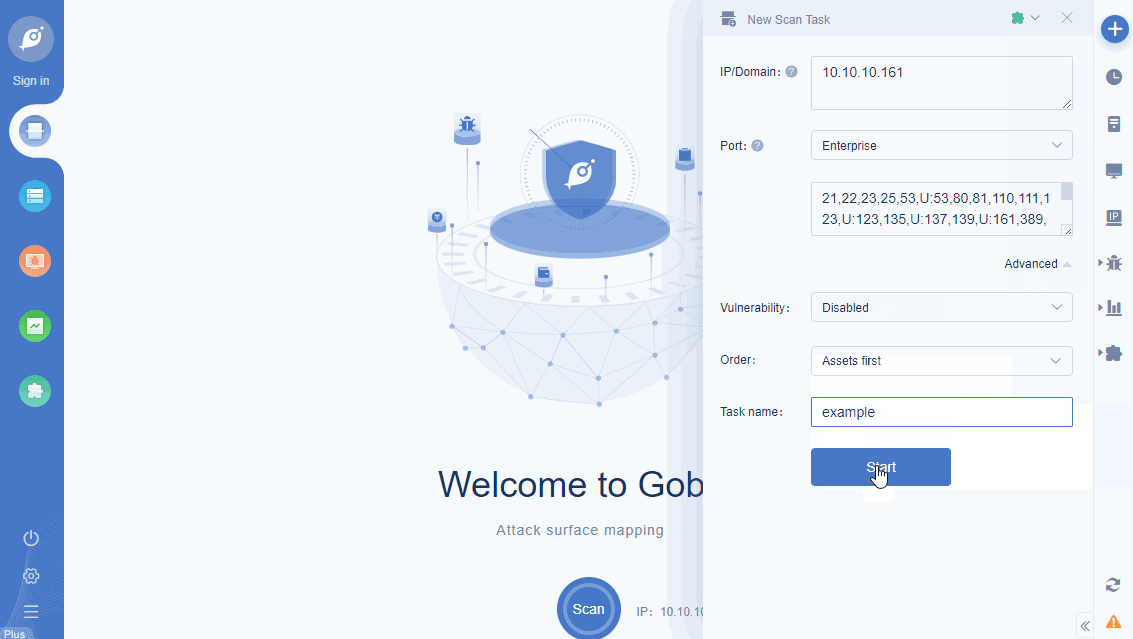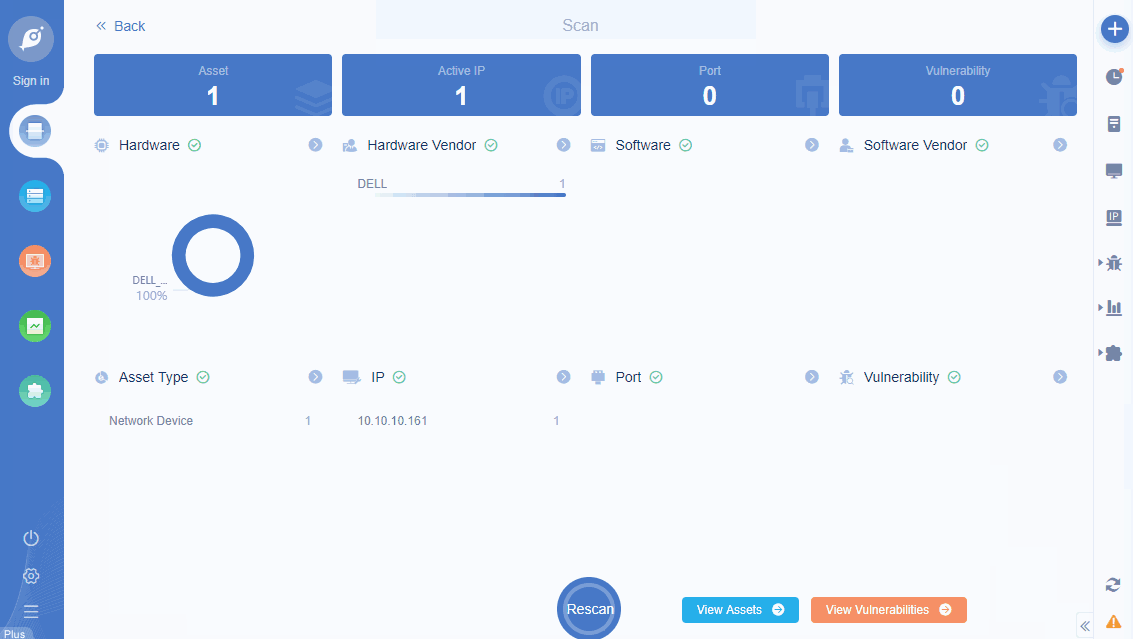
• New extensions: 1. SubDomainsBrute; 2. Deserialization vulnerability exploit tool and Deserialization the vulnerability Payload generator. • Added cookie access: Unauthorized logins automatically set cookie access. • Support for task naming: It helps to distinguish multiple tasks by naming them after the note task information. • Support all ports display and export. • New protocols: added dubbo, dtls, t3, htcpcp, etc. • Enhanced protocol identification, enhanced SSH protocol and L2TP protocol for more information extraction. • New vulnerabilities: CNNVD-202004-1959, CVE-2019-11510, CNVD-2019-32204, CNVD-2019-16798, CVE-2020-5902, CVE-2010-0219, Weaver e-cology OA Database config leakage, CVE-2020-3452, CNVD-2019-34241, CNVD-2019-29902. • Fixed VPN unable scan problem such as Sangfor. • Fixed smb and tomcat weak password are inaccurately reported. • Optimized server performance to fix Shell service instability. • Fixed some display problems.
SubDomainsBrute
• Preset 3000 dictionaries, after input root domain, Start cracking.

• Custom dictionary: Configure the full path of the dictionary, such as: E:\test\src\dict.txt.
Notice: Custom dictionary must be TXT file, newline split.↓

Cookie access

New vulnerabilities

Beta1.7.186
3 years agoIn this update
• New 1000+ fingerprint rules: expand the scale of enterprise-level application recognition. • Added extension market: Linked with FOFA query and MSF modules to enhance asset collection and vulnerability verification functions. And open to the community, support user-defined extemsions. • Support product version recognition: it helps to sort out assets more accurately. • Support import/export PoC in batch: It is convenient for data migration when Goby version is updated or computer environment is changed. • New vulnerabilities: CVE-2020-9296, CVE-2020-5410, CVE-2017-11610, CNNVD-202004-1959. • Added SNMP/TCP brute force cracking. • Fixed the inaccuracy of Fortios exploit module. • Fixed some display problems.
Extensions
Developer’s guide:https://gobies.org/docs.html

• Extensions-FOFA
The IP and port of the target are queried through FOFA, and put into Goby for scanning.

• Extensions-MSF
You need to install the Metasploit environment. For demonstration purposes, only the process of utilizing modules is currently implemented.

• Extensions-ExportCsv

• Extensions-Http

New vulnerabilities

CVE-2020-9296 Demo

Product version recognition

Import/export PoC in batch

Beta1.6.154
3 years agoIn this update
• New exploitable vulnerabilities: CVE-2020-11651, CVE-2020-12116, CVE-2020-11710, CVE-2019-3799, CVE-2018-13379, CVE-2017-17215, CVE-2016-4437, Druid not certified information leakage vulnerability, Improper configuration of Spring Boot actuator leading to information leakage, Improper configuration of Spring Boot Admin leading to unauthorized access vulnerability. • Added 2 sets of anime themes to increase the fun of Goby. • Support dial VPN mode scanning and vulnerability verification. • Fixed file merge issue on MacOS. • Fixed Goby startup crash issue caused by permission issues on Windows.
New vulnerabilities

Beta1.6.144
3 years agoIn this update
• New personalized theme: you can choose your favorite theme template. • Fast PoC management: Before scanning, PoC management can be performed to check preset vulnerabilities and custom PoC. • One-click rescanning: After the scan is completed, rescan directly by the scan progress button, without returning to the task initial interface. • Add URL to asset list page: no need to enter IP details page to view, more convenient. • Add body content crawling: Quickly obtain website feature information, no need to open URL one by one. • Add protocol configuration switch: support scanning and prohibiting scanning of intranet protocols MDNS and UPnP. • Support keyboard ESC key to quickly close all form pop-ups. • New vulnerabilities: CVE-2020-7961, CVE-2019-3948.
Personalized theme



Body content

CVE-2020-7961
Vul name:Liferay Portal Java Unmarshalling via JSONWS RCE
FOFA Dork:app="Liferay"
EXP:Yes

Beta1.6.138
4 years agoIn this update
• Scan assets by vulnerabilities: batch detection for a single vulnerability.
• Export task results to Excel format quickly: in the asset list / vulnerability list / history task pop-up window, you can directly and quickly export task data to excel format.
• Added authentication socks5 proxy: support proxy connection with or without password, more concealed and safe during operation.
• New exploitable vulnerabilities: CVE-2020-7247, HYBRID DVR RCE.
• Fixed some MacOS issues: Mac prompts for access permission and cannot put Goby in application directory, etc.
• Fixed some crash issues: Crash issues when using Window to scan, etc.
Scan assets by vulnerabilities

Authentication socks5 proxy

Export task results to Excel format quickly