Stelligent CloudFormation Templates
Purpose
This repository contains a collaboration of general and specific Amazon Web Services CloudFormation Template Examples.
The basic design is a layered approach so there is less repeat content between all the templates.
That way you can build a custom environment by picking the solution templates you wish to use.
In other words you won't see a VPC created over and over throughout the templates.
You simply use the VPC template then move to the next piece you would like to create.
Also, The general design leans towards not having to refactor the template to fit your account/environment.
By using the configured parameters from the console or CLI you should be able to use the template without the need to edit it.
The templates generally output all the information you may need for another template.
So, be sure to examine the Outputs tab after creating the stack.
The AWS CLI examples can be dropped in a shell script and/or added to your CI/CD solution to spin up solutions in a fully automated fashion.
Of course logic around updating stacks, deleting and checking for success/failure should be addressed.
With a simple shell script and a customized parameter json file you can spin up stacks quickly and consistently.
Furthermore it's just as easy to tear a CloudFormation stack versus if all the objects where created manually.
Templates
Categories
Orchestrators
Back to Top
One template to rule them all... These are master templates that call nested templates.
These are good to build out a full environment without having to run each template individually.
Coupled with a custom parameters JSON file can give you a one command solution to a complex setup and eliminate the need to duplicate code.
For instance you could have a VPC, NAT, RDS and Autoscaling Webapp behind an ELB and Update DNS all in one
command using various foundational templates that I've creates to be used together.
|
|
Select the foundational pieces for building out an infrastructure from the ground up.
Create Details
- VPC
- Nat Gateway (Optional)
- Bastion Host (Optinoal)
- VPN (Optional)
Public S3 URL
https://s3.amazonaws.com/stelligent-public/cloudformation-templates/github/infrastructure.yml
|
| Launch |

|
| View in Designer |

|
|
Infrastructure
Back to Top
|
|
Creates a single Bastion host on a Public subnet in an existing VPC. Select from either a RHEL, Ubuntu or Windows OS.
Prerequisites
- VPC
- Public Subnet, IGW, Private Subnet/s.
- Either use an existing VPC Infrastructure or you can use the following VPC Template to create a one.
Available EIP
Create Details
- EC2 Instance
- EIP
- IAM Role
- IAM Instance Profile
- Security Group
Public S3 URL
https://s3.amazonaws.com/stelligent-public/cloudformation-templates/github/bastion.yml
|
| Launch |

|
| View in Designer |

|
|
|
|
Create EC2 Single Proxy Instance
Prerequisites
- VPC
- 1 Public Subnet
CloudFormation Tasks
- Create Single EC2 Instance on Public Network with Public IP
- Create Autoscaling Group of 1 for DR
- Create Proxy Access Security Group
- Install Chef Client
- Create Chef Configurations Files (environment, roles, etc.)
- Download Cookbooks from Github Repo
- Checkout Specific Version of Cookbook
- Run Chef Client using Chef Zero
- Warm EBS Volume
Chef Cookbook Tasks
- Install, Configure and Start Squid Proxy
- Setup CloudWatch Logs
- Create Route53 DNS Update Script
- Configure DNS Update Cron Job
Public S3 URL
https://s3.amazonaws.com/stelligent-public/cloudformation-templates/github/proxy-awsapi-devops-access.yml
|
| Launch |

|
|
Storage
Back to Top
|
|
Creates an Elastic File System with 3 Mounts
Prerequisites
- VPC
- 3 Subnets
Create Details
- EFS Filesystem
- 3 Mount Targets
Public S3 URL
https://s3.amazonaws.com/stelligent-public/cloudformation-templates/github/efs.yml
|
| Launch |

|
|
|
|
Create S3 Backup Bucket
Prerequisites
- VPC
- VPC Endpoint
Create Details
- Single S3 Bucket
- Enabled Versioning
- Enforced Encryption
- Creates LifeCycle to Delete Previous Versions after X Days
Public S3 URL
https://s3.amazonaws.com/stelligent-public/cloudformation-templates/github/s3-backup-bucket-delete-previous.yml
|
| Launch |

|
|
Database
Back to Top
|
|
Creates a MySQL RDS Database Instance.
Prerequisites
- VPC
- Public Subnet, IGW, Private Subnet/s.
- Either use an existing VPC Infrastructure or you can use the following VPC Template to create a one.
Create Details
- DB Instance
- DB Subnet Group
- Security Group
- Cloud Watch Alarms
- Route 53 Record Set (Optional)
Public S3 URL
https://s3.amazonaws.com/stelligent-public/cloudformation-templates/github/mysql-rds.yml
|
| Launch |

|
|
|
|
Creates an RDS Instance From Snapshot. Can be great for Blue/Green or pull Prd DB to Nonprod for testing.
Prerequisites
- RDS Snapshot in Same Region
- 2+ Subnets if Enabling Multi AZ
Create Details
- Create RDS Instance from Snapshot
- Create Subnet Group
- Create Access Security Group
- Optionally Configure DNS Record in Route53
Notes
- Because it's a restore several options are not available. Such as:
- Can't set Master User and Password
- Can't select what DB Engine
- Can't set allocated storage
Public S3 URL
https://s3.amazonaws.com/stelligent-public/cloudformation-templates/github/create-rds-from-snapshot.yml
|
| Launch |

|
|
Autoscaling
Back to Top
|
|
Create an Autoscaling group in 3 private subnets from a baked AMI, an Elastic Load Balancer in 3 public subnets and S3 ELB Logging Bucket.
Option to use SSL/TLS on ELB. Option to update Route 53 Hosted DNS alias to point to the ELB.
Setup to add RDS Access Security Group. Does not create an RDS Instance. Use an RDS Instance Cloudformation Template first.
Create Details
- EC2 Instances
- AutoScaling
- Launch Configuration
- Elastic Load Balancer
- IAM Role
- IAM Instance Profile
- Security Group
- Scale Up Policy
- Scale Down Policy
- Cloud Watch Alarm
- Network ACL Entry
- Route 53 Record Set (Optional)
- S3 Bucket (Optional)
- S3 Bucket Policy (Optional)
Public S3 URL
https://s3.amazonaws.com/stelligent-public/cloudformation-templates/github/autoscaling-bakedami-rdsbackend.yml
|
| Launch |

|
| View in Designer |

|
|
Labs
Back to Top
|
|
Automates the integration between AWS Lambda and CodePipeline
Prerequisites
- N/A
Supported Regions
- us-east-1
Create Details
- IAM Policy and Roles
- Lambda Function
- CodePipeline
|
| Launch |

us-east-1
|
| View in Designer |

|
|
|
|
Creates a Bitbucket Server in a private or public subnet in an existing VPC.
Prerequisites
- VPC
- Public or Private Subnet
- Internal Instance Access Security Group
- Either use an existing VPC Infrastructure or you can use the following VPC Template to create a one.
Internet Access from the EC2 Instance or Yum access solution
EC2 Key Pair
Available EIP if Selected Public Facing
IAM Role Creation Permissions
Supported Regions
- cn-north-1
- us-east-1
- us-west-1
- us-west-2
- eu-west-1
- eu-central-1
- ap-northeast-1
- ap-northeast-2
- ap-southeast-1
- ap-southeast-2
- sa-east-1
Create Details
- EC2 Instance (Amazon Linux)
- EIP (Optional)
- IAM Role
- IAM Instance Profile
- Security Group
Public S3 URL
https://s3.amazonaws.com/stelligent-public/cloudformation-templates/github/bitbucket.yml
|
| Launch |

|
| View in Designer |

|
|
|
|
Creates a Chef Complianc Web server in a Public Subnet with Internet Gatewayy attached on an existing VPC.
It then attaches an EIP and finally adds the instance to an existing instance-to-instance security group.
Prerequisites
- VPC
- Public Subnet, IGW, Private Subnet/s.
- Either use an existing VPC Infrastructure or you can use the following VPC Template to create a one.
Available EIP
Supported Regions
- us-west-2
- us-east-1
Create Details
- EC2 Instance
- EIP
- IAM Role
- IAM Instance Profile
- Security Group
Public S3 URL
https://s3.amazonaws.com/stelligent-public/cloudformation-templates/github/chef-compliance.yml
|
| Launch |

|
| View in Designer |

|
|
|
|
Automates the integration between AWS CodeBuild, CodeCommit, CodeDeploy, and CodePipeline
Prerequisites
- EC2 Key Pair
Supported Regions
- us-east-1
Create Details
- IAM Roles
- EC2 instance (for CodeDeploy)
- CodeCommit
- CodeDeploy
- CodePipeline
|
| Launch |

us-east-1
|
| View in Designer |

|
| How To Video |

|
|
|
|
Automates the integration between AWS CodeCommit and CodePipeline
Prerequisites
- EC2 Key Pair
- CodeCommit Repo
Supported Regions
- us-east-1
Create Details
- IAM InstanceProfile, Policy, and Roles
- EC2 Instance for CodeDeploy
- CodeDeploy
- CodePipeline with CodeCommit Integration
|
| Launch |

us-east-1
|
| View in Designer |

|
|
|
|
Adds a Manual Approval to a CodePipeline
Prerequisites
- CodeCommit Repository
Supported Regions
- us-east-1
Create Details
- IAM Policy and Roles
- AWS Lambda Function
- SNS
- CodePipeline
|
| Launch |

us-east-1
|
| View in Designer |

|
| How To Video |

|
|
|
|
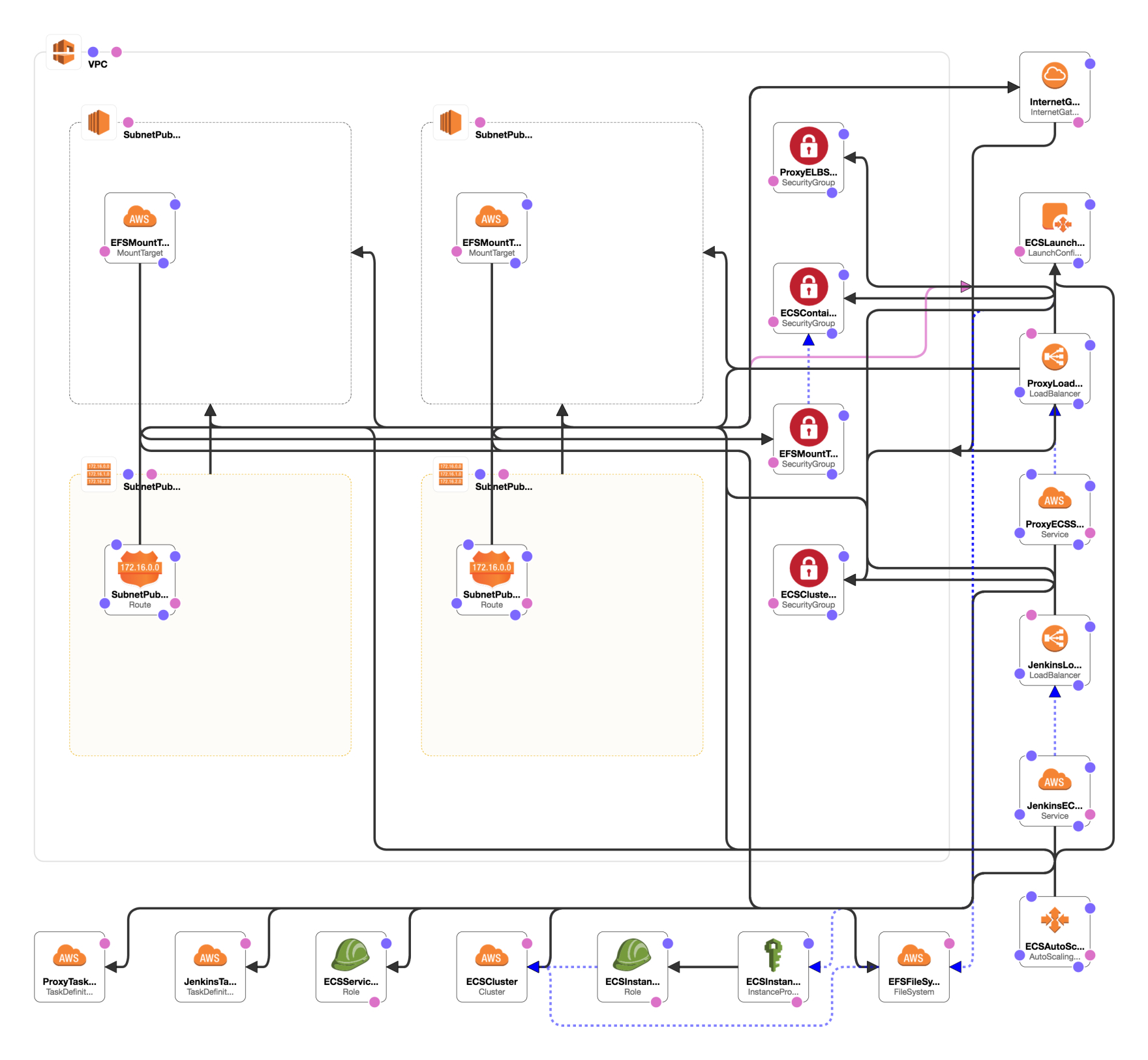
Containerized CI Solutions in AWS: Jenkins in ECS
Prerequisites
- EC2 Key Pair
Supported Regions
- us-east-1
Create Details
- VPC and associated resources
- IAM
- EFS
- EC2 Instances
- Auto Scaling
- ELB
- ECS Service, Cluster, Task Definition
|
| Launch |

us-east-1
|
| View in Designer |
|
|
|
|
Automates the integration between EC2 Container Service (ECS), EC2 Container Registry (ECR), CodeCommit, and CodePipeline
Prerequisites
- EC2 Key Pair
- Existing Docker Image
- CodeCommit Repository
- ECR Repository
Supported Regions
- us-east-1
Create Details
- Virtual Private Cloud (VPC) (and associated resources)
- Auto Scaling Group, Auto Scaling Launch Configuration
- ECS Cluster, ECS Service, ECS Task Definition
- Elastic Load Balancer
- IAM Instance Profile, IAM Roles
- EC2 Instance (Jenkins, Docker)
- CodePipeline with CodeCommit Integration
|
| Launch |

us-east-1
|
| View in Designer |

|
|
|
|
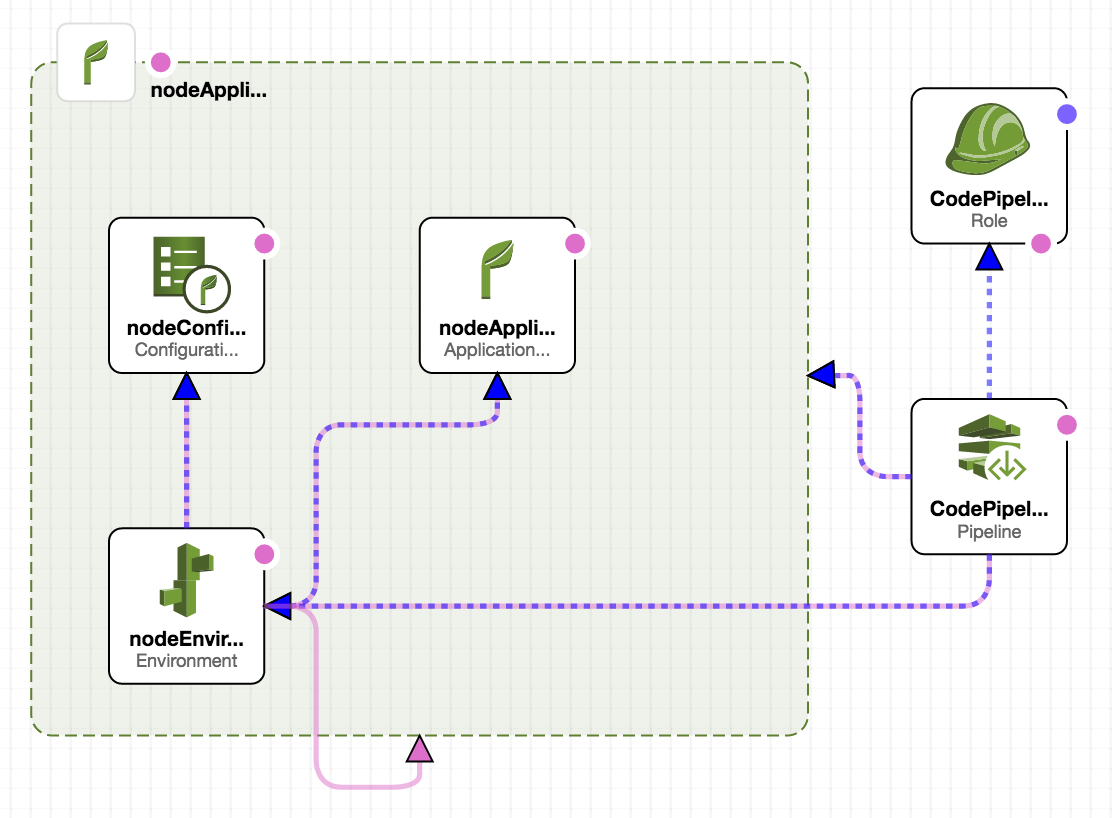
Automates the integration between AWS Elastic Beanstalk and CodePipeline
Prerequisites
- CodeCommit Repo
Supported Regions
- us-east-1
Create Details
- IAM InstanceProfile, Policy, and Roles
- Elastic Beanstalk - ConfigurationTemplate, Environment
- CodePipeline with CodeCommit Integration
|
| Launch |

us-east-1
|
| View in Designer |
|
|
|
|
Create S3 Backup Bucket
Prerequisites
- VPC
- Public Subnet
- Internal Access Security Group
- RDS Security Group
- EFS Security Group
Create Details
- Single Amazon Linux EC2 Instance
- Create Web Access Security Group
- Create IAM Instance Profile Role
- Create CloudWatch Logs Group
- No External IP
Deploy Details
- Installs Nginx
- Installs PHP-FPM 7.0
- Installs MySQL 5.6 Client
- Installs Specfic Release of Mediawiki (Default REL1_28)
- Installs Creates Nginx Config for Mediawiki
- Assumes RDS Backend
- Assumes EFS Shared Content Mount
|
| Launch |

|
|
|
|
Creates a deployment pipeline in AWS CodePipeline using a pre-built Lambda function. It can be used to model a pipeline without initial implementation
Prerequisites
- AWS Account
Supported Regions
- us-east-1
Create Details
- Amazon S3 bucket for CodePipeline artifacts
- AWS SNS Topic
- AWS IAM Policy and Roles
- AWS Lambda Function
- AWS CodePipeline Stages and Actions
|
| Launch |

us-east-1
|
| View in Designer |

|
|
|
|
Automates the integration between AWS OpsWorks, CodeCommit and CodePipeline
Prerequisites
- EC2 Key Pair
Supported Regions
- us-east-1
Create Details
- IAM InstanceProfile, Policy, and Roles
- SecurityGroupIngress and SecurityGroup
- OpsWorks Stack, Layer, App and Instance
- CodePipeline
|
| Launch |

us-east-1
|
| View in Designer |

|
|
|
|
Creates an S3 bucket to host a single-page application and a continuous delivery pipeline with CodeBuild and CodePipeline.
Prerequisites
- GitHub token (with access to repo and admin:repo_hook)
Supported Regions
- us-east-1
- us-west-2
Create Details
- IAM Role for CodePipeline
- IAM Role for CodeBuild
- S3 Bucket
- CodeBuild Project
- CodePipeline Project
|
| Launch |

us-west-2

us-east-1
|
|
|
|
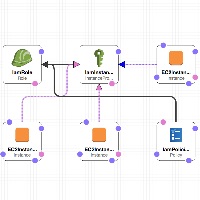
Creates three test instances in an existing VPC. Each instance is a different operating system. They are; Red Hat Enterprise Linux 7, Ubuntu 14 and Windows 2012 R2.
Create Details
- 3 EC2 Instances
- IAM Role
- IAM Instance Profile
Public S3 URL
https://s3.amazonaws.com/stelligent-public/cloudformation-templates/github/rhel-ubuntu-win2012.yml
|
| Launch |

|
| View in Designer |
|
|
|
|
Create S3 Backup Bucket
Prerequisites
- VPC
- Public Subnet
- Internal Access Security Group
- RDS Security Group
- EFS Security Group
Create Details
- Single Amazon Linux EC2 Instance
- Create Web Access Security Group
- Create IAM Instance Profile Role
- Create CloudWatch Logs Group
- No External IP
Deploy Details
- Installs Nginx
- Installs PHP-FPM 7.0
- Installs MySQL 5.6 Client
- Installs Latest Wordpress
- Installs Creates Nginx Config for Wordpress
- Assumes RDS Backend
- Assumes EFS Shared Content Mount
|
| Launch |

|
|
Back to Top